

For a user to log into SecureAnyBox, the user needs to be created and has a password entered.
If more than one domain is specified, the user must also enter the domain name when logging in.

Only one domain is specified. You only need to enter your username and password to sign in to SecureAnyBox.
More than one domain is specified. You must also enter a domain name to log into SecureAnyBox.
After entering the login credentials, a page for setting an access code displays. The access code is used to decrypt secure information (such as passwords, certificates) and to confirm changes.
While entering the access code, you can see how secure your access code is and also how many of the required characters you are using.

Actual/required length of the access code
Actual/required number of lowercase letters
Actual/required number of uppercase letters
Actual/required number of numbers
Pointer how secure the access code is
Button for displaying the access code
Time to crack the access code online
Actual/required entropy of the access code (the higher, the better)
Requirements to characters of the access code can be changed in the Configuration for users in all domains or in the domain details for users in that domain.
After the access code set, the page automatically redirects to the root level of Safe Boxes.

Full name of the logged user and a domain into which the user logged
After clicking on the menu icon (next to the name of the user), a context menu displays. In the context menu, it is possible to change user’s settings, activate the White Envelope or log out from the application.
Notification area
If any error or warning occurs or some action needs to perform, the notification displays in the area. For more information, please click the notification icon.
Main menu
The main menu of the application. Displayed menu items are dependent on the user’s role and other settings.
Information about license
Information about license displays only to users with the “Administrator” role.
Breadcrumb navigation
The breadcrumb navigation shows a path to the currently opened page. By clicking on the breadcrumb navigation element, it is possible to move to the parent level.
Page menu
The list of possible actions on the page.
Filter area
Enables filtration of items displayed on the page.
If you know your access code, and you need to change it (due to security reasons or you shared your access code with someone else, etc.), please click the menu icon (next to a name of the user) in the top right corner of the page (
![]() ). After clicking, a context menu displays. In a menu, please click on the
Change Access Code
button (
). After clicking, a context menu displays. In a menu, please click on the
Change Access Code
button (
![]() ).
).

After clicking the button, a form for changing the access code displays. To change the access code enter a current access code into the first field and into other two fields, please enter a new one. While entering the new access code, you can see how secure your access code is and also how many of the required characters you are using.

To confirm the new access code, please click the OK button. After the new access code set, a success message displays.

In a case you forgot the access code, you may reset it. By resetting your access code, you will lose access to all Safe Boxes, and Safe Boxes accessed only by you will be deleted.
Before reset of the access code, please consult your administrator about losses.
To reset the access code, please click the menu icon (next to the name of the user) in the top right corner of the page (
![]() ). After clicking, a context menu displays. In a menu, please click the
Reset Access Code
button (
). After clicking, a context menu displays. In a menu, please click the
Reset Access Code
button (
![]() ).
).

You need to confirm the warning only if you have access to some Safe Box. Otherwise, you will be asked to enter a new access code immediately.
In the Reset Access Code form, you must confirm the warning that you will lose access to all Safe Boxes. You can also check which Safe Boxes will be deleted because after the access code restored, nobody will have permission for these Safe Boxes.

After the warning confirmed, a form for entering new access code displays. While entering the access code, you can see how secure your access code is and also how many of the required characters you are using. To confirm the new access code, please click the OK button.

After resetting the access code, you will see a message about the successful reset of the access code. You can confirm the changes with the new access code. If you had some inherited permissions for Safe Box Groups and Safe Boxes, another user could share them to you. Also, your White Envelope can be activated again, but all assigned permissions have to be assigned manually.

LDAP synchronized users are not allowed to changing their password in the SecureAnyBox because the password does not change in LDAP. If you are not sure whether you are syncing from LDAP, contact your administrator and consult the password change.
To change your login password, please click on the menu icon (next to a name of the user) in the top right corner of the page (
![]() ). After clicking, a context menu displays. In a menu, please click on the
Change Login Password
button (
). After clicking, a context menu displays. In a menu, please click on the
Change Login Password
button (
![]() ).
).

After clicking the button, Change Login Password form displays. To change your login password, please enter the current password into the first field and to the other fields enter a new one. While entering the new password, you can see how long your password is, how many lowercase letters, uppercase letters, numbers or other symbols password contains and how secure your password is.

To confirm the change of the password, please click the OK button. After changing the password, a success message displays.
In order to improve the security of data stored in the SecureAnyBox, users can use Two-Factor Authentication. As a second factor is used 6-digits code from the Authenticator app, paired with SecureAnyBox via secret-key.
Each user can enable two-factor authentication to SecureAnyBox. If the Two-Factor Authentication is enabled, the user has to enter a verification code every time to log in. Verification code is generated by the Authenticator app on the users mobile phone (iOS and Android).
To enable a Two-Factor Authentication, it is necessary to have the Authenticator app installed on a mobile phone.
To enable the Two-Factor Authentication, please click on the menu icon (next to the name of the user) in the top right corner of the page (
![]() ). After clicking, a context menu displays. In the displayed menu, please click on the
Two-Factor Authentication settings
button (
). After clicking, a context menu displays. In the displayed menu, please click on the
Two-Factor Authentication settings
button (
![]() ).
).

After clicking the button, a wizard displays. To enable a Two-Factor Authentication is necessary to pair the Authenticator app with SecureAnyBox. Please follow the steps in the wizard.




After the Two-Factor Authentication set, a user has to enter the second factor every time to log in. Two-Factor Authentication can be deactivated by the user in the Two-Factor Authentication settings or by user with the User Manager role in the user’s details.
Once the Two-Factor Authentication set and confirmed, it is possible to pair another Authenticator.
To pair another Authenticator, please click on the menu icon (next to the name of the user) in the top right corner of the page (
![]() ). After clicking, a context menu displays. In the displayed menu, please click on the
Two-Factor Authentication settings
button (
). After clicking, a context menu displays. In the displayed menu, please click on the
Two-Factor Authentication settings
button (
![]() ).
).

After clicking the button, the wizard with two options displayed. Please click the PAIR ANOTHER AUTHENTICATOR button and follow the steps. When another Authenticator paired, all Authenticators should give you the same 6-digit code.





If you do not want to use the second factor, you can disable Two-Factor Authentication settings. But in a case, that the Two/Factor Authentication is mandatory, you will be ask to set the second factor again. Disabling the second factor will delete all user’s settings and all paired Authenticators have to be paired again.
To disable second factor, please click on the menu icon (next to the name of the user) in the top right corner of the page (
![]() ). After clicking, a context menu displays. In the displayed menu, please click on the
Two-Factor Authentication settings
button (
). After clicking, a context menu displays. In the displayed menu, please click on the
Two-Factor Authentication settings
button (
![]() ).
).

After clicking the button, the wizard with two options displayed. Please click the Disable second factor button and enter the 6-digit code to confirm the action.



Users with the User Manager role can reset Two-Factor Authentication settings for another user by clicking the Reset Two-Factor Authentication button in the bottom of user details form.

To confirm the reset is necessary to enter the access code. Reset of Two-Factor Authentication settings should use when the user lost access to the paired Authenticator app and etc.
Each user can change the language of a web interface. Available options are English, Czech, German and French. To change the language of the interface, please click on the menu icon (next to the name of the user) in the top right corner of the page (
![]() ). After clicking, a context menu displays. In the displayed menu, please click on the
Change Language
button (
). After clicking, a context menu displays. In the displayed menu, please click on the
Change Language
button (
![]() ).
).

After clicking the button, a form for changing the language displays. In the form, please select which language you want to set, and click the OK button. After changing the language, a page reloads in the chosen language.

Each user can modify preferences, which are applied only to him. To alter these preferences, please click on the menu icon (next to the name of the user) in the top right corner of the page (
![]() ). After clicking, a context menu displays. In the displayed menu, please click the
Change preferences
button (
). After clicking, a context menu displays. In the displayed menu, please click the
Change preferences
button (
![]() ).
).

After clicking on the Change Preferences button, User preferences form displays.

Field
Remember Access Code
(
![]() ) is displayed only if remembering of Access Code is set in the server configuration.
) is displayed only if remembering of Access Code is set in the server configuration.
Fields in
Notification settings
part of a form (
![]() ) are displayed if e-mail notifications are enabled in the server configuration.
) are displayed if e-mail notifications are enabled in the server configuration.
Field
Notification of user initialization
(
![]() ) is displayed only to users with
User Manager role.
) is displayed only to users with
User Manager role.
In User preferences form, it is possible to set remembering last location, default password pattern for Safe Box Groups, Safe Boxes, and Accounts which user will create and configure e-mail notification settings. All preferences are applied only for the currently logged user. Changing preferences for all users is possible in SecureAnyBox configuration.
If a start page set, it is not possible to set the remembering of the last visited location.
This field is displayed if remembering of Access Code is set in the server configuration.
After entering an Access Code, SecureAnyBox will temporarily store your Access Code in a cache, so you don’t have to enter the Access Code repeatedly. To disable remembering your Access Code, uncheck the field.
Default password pattern for Safe boxes and Accounts where no password pattern is set.
Each letter in the pattern corresponds to letter in the generated password.
See examples of the password pattern
Characters allowed in the password pattern and their meaning:
v – lower case vowel a,e,i,o,u,y
V – mixed case vowel (A,E,I,O,U,Y,a,e,i,o,u,y)
Z – upper case vowel
c – lower case consonant (b,c,d,f,g,h,j,k,l,m,n,p,q,r,s,t,v,w,x,z)
C – mixed case consonant
z – upper case consonant
l - any alphabet character (vowel or consonant) - lower case
A - any alphabet character - mixed case
u – upper case alphabet
d - digit (0-9)
s – special character (.,@,&,*,(,),<,>,_,],[,%,$,#,\,/,?,;,-,:)
n – digit or special character
\ - escape character - next character is used as is (e.g pattern ‘\-‘ outputs ‘-‘ in the resulting password)
* - any allowed character
Default pattern is CVCVdddCVCCVdC (this might generate passwords such as: wEHe063heFme4p)
For example, you can set password pattern as ‘\p\a\s\sddddddd‘ and this might generate password such as ‘pass1762885‘ or ‘pass5687412‘.
Selection of which data displays in the middle column of the list of records in the Safe Box – after the record name. The default value in server configuration is Description.
This field is displayed only if e-mail notifications are enabled in the server configuration.
Select if notification e-mails with a summary of changes will be sent and whether you will be notified of changes in all in Safe Box Groups, Safe Boxes, and records, or only the watched ones.
Whether users will be notified of changes in all fields or only encrypted ones and how often notification will be sent to them depends on SecureAnyBox server configuration.
This field is displayed only if e-mail notifications are enabled in the server configuration.
Select if notification e-mails with a summary of accesses to encrypted information will be sent and whether you will be notified of accesses to encrypted information in all currently accessible Safe Box Groups, Safe Boxes, and records, or only the watched ones.
How often notification will be sent to users depends on SecureAnyBox server configuration.
This field is displayed only if e-mail notifications are enabled in the server configuration.
This field is displayed only to users with
User Manager role.
Enabling e-mail notifications of user initialization, you will allow sending emails with a summary of which user set their password and/or Access Code for the first time.
By overriding the default settings from the domain, you can set the automatic watching accordingly on your preferences. If the default setting overridden, any changes in settings of automatic watching in the domain will not apply to you.
For Safe Box Groups, Safe Boxes, and records, the user creates or obtains access will be set watching changes automatically. If sending notifications is enabled (in the server configuration), e-mail notifications will be sent with a summary of changes in the watched ones.
Safe Box Groups, Safe Boxes, and records, the user creates or obtains access will be automatically watching accesses to encrypted information in them. If sending notifications is enabled (in the server configuration), e-mail notifications will be sent with a summary of accesses to the watched ones.
Each user can set a start page – page to which will be redirected after login into SecureAnyBox.
To set start page, please click on the menu icon (next to the name of the user) in the top right corner of the page (
![]() ). After clicking, a context menu displays. In the displayed menu, please click the
Start page setting (
). After clicking, a context menu displays. In the displayed menu, please click the
Start page setting (
![]() ).
).

After clicking Start page setting , window for start page setting displays.
If you are setting up a start page for the first time, a window will appear where you confirm that you want to set the page as a start page.

In a case, the current page is set as a start page, a window will appear where it is possible to remove start page setting.

If a start page is set to different page than the current page, it is possible to check setting by clicking the link. At the same time, you can override or remove your start page settings.

From version 5.0, the Administration part of SecureAnyBox has been moved to its own interface. To switch to Administration, please click on the menu icon (next to the name of the user) in the top right corner of the page (
![]() ). After clicking, a context menu displays. In the displayed menu, please click the
Switch to Administration (
). After clicking, a context menu displays. In the displayed menu, please click the
Switch to Administration (
![]() ), which will redirect you to the Administration interface.
), which will redirect you to the Administration interface.

Safe Boxes and Safe Box Groups are used to store sensitive data, such as accounts used to log in, certificates, credit cards, and other files. Safe Boxes can be divided into three types:
Safe Boxes and Safe Box Groups can be shared with other users. On shared Safe Boxes and Safe Box Groups will apply dynamic inheritance of permissions. For private Safe Boxes and SafeBox Groups, all permissions to other users have to be set manually.
Each name of Safe Box or Safe Box Group must be unique within the range of root level or Safe Box Group. However, is possible to create private Safe Box or Safe Box Group with the same name as another Safe Box (or Safe Box Group), because the private Safe Box’s name contains an owner’s name.
When the logged user is an owner of a private Safe Box, he can’t see the owner’s name in s Safe Box’s name.

As you can see in the image above, Private Safe Box’s name is displayed differently to the owner of private Safe Box and to other users who have permissions to this private Safe Box.
p(#FilteringOfSafeBoxesAndSafeBoxGroupsParagraph1).Safe Boxes and Safe Box Groups at the root level can be filtered by their name or description by entering a text into the filter field (
![]() ). Safe Boxes and Safe Box Groups can also be filtered by selecting a user tag or a user into a special field (
). Safe Boxes and Safe Box Groups can also be filtered by selecting a user tag or a user into a special field (
![]() ).
).

When filtering by a user tag, in the table are shown Safe Boxes and Safe Box Groups which have some permission template assigned to the selected user tag.
When filtering by user, the table shows Safe Boxes and Safe Box Groups to which the selected user has some permissions.
User can edit order of displayed Safe Boxes and Safe Box Groups by pinning the selected Safe Box (Safe Box Group) to the top of the list.
To pin the Safe Box, please click the pin icon (
![]() ) in the row of selected Safe Box, and confirm the dialog.
) in the row of selected Safe Box, and confirm the dialog.


After the Safe Box is pinned, it displays at the top of the list with pin icon.

Order of pinned Safe Boxes can be managed in the form, which displays after clicking the Edit pinned order button. To change the order of the pinned Safe Boxes, drag the selected Safe Box to the desired position.

To unpin the Safe Box, please click the pin icon again and confirm the dialog. After unpinning, the Safe Box is displayed without the pin icon.
Access rights can be managed for each Safe Box or Safe Box Group separately. For Safe Boxes and Safe Box Groups, which are not private applies the dynamic inheritance of access rights. If Safe Box or Safe Box Group is private, then inheritance of access rights is blocked. However, permissions for the private Safe Box Group or Safe Box can be assigned manually.
Access rights can be managed at the root level too.
Managing of the access rights is possible after clicking on a link
Sharing & Permissions
.
The Sharing & Permissions button is displayed only to users with permission Access Control

At the page Sharing & Permissions is displayed a table of users who have permissions for that level (the root level, a Safe Box Group or Safe Box) and all records in it.
Each user can have three types of rights:
Inherited rights - Permissions inherited from parent Safe Box Group or the root level
Effective rights - These permissions are checked when verifying permissions to some action. Effective rights are given by assigned rights. If rights not assigned, then effective rights are given by from inherited rights. If a user has effective rights to READ for any of Safe Boxes inside a Safe Box Group, then effective rights for the Safe Box Group will be set to READ as well. In a case, that a Safe Box or a Safe Box Group is private, the owner’s effective rights will be set to full permissions (IRCMDA).
Assigned rights - Permissions explicitly assigned
In a table are displayed only permissions which can be set at the Sharing & Permissions page.
| Permission | Description |
|---|---|
| Inherited | This permission enables dynamic inheritance of permissions. Can be set only for the root level or a Safe Box Group |
| Read | User has permission to view Safe Box Groups, Safe Boxes and records in them (accounts, files, etc.) |
| Create | User has permission to create new Safe Box Group, Safe Box or record (account, file, etc.) |
| Modify | User has permission to modify Safe Box Groups, Safe Boxes and records in them (accounts, files, etc.) |
| Delete | User has permission to delete or move Safe Box Group, Safe Box or record (account, file, etc.) |
| Access Control | User has permission to manage rights for Safe Box Group, Safe Box or record (account, file, etc.) |
| Apply Templates | User has permission to apply Permission templates for Safe Box Group or SafeBox. |
By assigning access rights, you can share a Safe Box or Safe Box Group with other users.
To assign permissions for Safe Box or Safe Box Group to another user, please click on the
Add User
button. After clicking, a list of users to whom is possible to share Safe Box or Safe Box Group displays. You cannot share Safe Boxes and Safe Box Groups with users who don’t have set the access code.
If a user is from a different domain than the currently logged user, after the user’s name is displayed a domain name.

In a list of users, please select a user with whom you want to share a Safe Box or Safe Box Group. It is possible to add multiple users at a time. After users are selected, please click the
OK
button. Adding users needs to be confirmed by entering the access code. Have you forgotten the access code?
After adding a user into a table of permissions, the user has only a permission to READ. You can assign other permissions manually by checking the appropriate checkbox.
All changes at the Sharing & Permissions’s page have to be confirmed by entering the access code.
The assigned rights can be managed separately for each Safe Box or Safe Box Group. If a user has any inherited rights, it is necessary to click on the blue gear icon (
 ). After that, it is possible to assign rights by clicking on an appropriate checkbox.
). After that, it is possible to assign rights by clicking on an appropriate checkbox.
Assigned rights have precedence before inherited ones.
If a user does not have any inherited rights, assigned rights can be managed just by clicking on an appropriate checkbox.
To delete assigned rights for a user, click on the icon of a cross (
![]() ) at the end of a row and confirm applying changes. If the deleted user had the assigned rights only, then after confirmation is no longer displayed in a table.
) at the end of a row and confirm applying changes. If the deleted user had the assigned rights only, then after confirmation is no longer displayed in a table.
Dynamic inheritance of permissions applies only to shared Safe Boxes or Safe Box Groups. To apply the dynamic inheritance of user access rights, the user must have assigned the Inherited permission for the root level or Safe Box Group.
When a user has the Inherited permission assigned for the root level, all of the user’s other permissions (Read, Create, Modify, Delete, Access Control) at the root level will be inherited by all shared Safe Boxes and Safe Box Groups.
If a user has the Inherited permission assigned only for a Safe Box Group, all of the user’s other permissions at a Safe Box Group will be inherited by all shared Safe Boxes within the range of Safe Box Group.
When a user modifies the Inherited permission, a warning dialog appears. To proceed with the modification, a user has to type in the confirmation code (three letters displayed boldly) and confirm the warning dialog.

Permissions for the root level are pre-set by Default Safe Box Permissions in a user detail but can be modified directly for the root level. To be able to manage permissions for the root level, logged user need to have Access Control permission for the root level and user role User Manager or Administrator. Otherwise, the Sharing & Permissions button is not going to be displayed at the root level page.

Permission templates can be managed only by users with permission Access Control
Permission templates are designed to help you assign permissions to users. Permission templates can set for root level, any Safe Box Group, and any Safe Box. Permission templates are set for user tags. For each level, you can create user tag one time only. User tags can be from the domain of the current user and even from other visible domains.

To create a permission template, please select user tag and assign permissions. Permission template will apply to all users with the same user tag as set in the template.
| Permission template set for | Affected levels |
|---|---|
| Root level | all shared Safe Boxes and Safe Box Groups |
| Safe Box Group | all Safe Boxes within the Safe Box Group |
| Safe Box | Safe Box only |
If the permission template set from the parent level, it is possible to modify it by clicking the blue gear icon (
 ).
).

To view or manage permission template(s) for parent level, click the
Up button.
After permission templates set, users with the permission
Apply templates
can apply them.
Only users with Apply templates permission can perform this action.
Permission templates can be applied when these conditions met:
When all conditions met, notification icon appears (
![]() )
)
Permission templates can be applied to Safe Box Group or Safe Box. Permissions to apply are computed based on permission template in listed Safe Box Groups and Safe Boxes for each user tag assigned to a user. If computed permissions are missing some of the effective permissions, the red arrow (
![]() ) appears.
) appears.

Please review permissions in the table below.
Permissions were computed based on Permission Templates in listed Safe Boxes and Safe Box Groups depending on User tags assigned to listed users.
You can either Approve permissions, Skip permission assignment this time or Reject permission assignment. When you Reject permission assignment, SecureAnyBox will remember this choice. Next time Permission Templates are processed, permission record will show as rejected by default.
To completely remove a user from the permission assignment processing, you can change the user’s user tag assignment.
| Computed permissions | Permissions applied to: |
|---|---|
| Contains permission I (Inherited) | all shared Safe Boxes and Safe Box Groups |
| Does not contain permission I | all shared Safe Boxes; Safe Box Groups will have just R (read) permission applied |
For Safe Box Groups, Safe Boxes, and records, it is possible to set the watching of changes and/or accesses to encrypted information. Watching can be set for each level – the only exception is the root level.
When a user is
watching changes for some level, and e-mail notifications are enabled in the server configuration, SecureAnyBox sends e-mails with a summary of changes at that level. Whether the changes are watched in all fields, or encrypted ones only, it depends on the server configuration of notifications.
If the user is
watching accesses to encrypted information and e-mail notifications are enabled in the server configuration, SecureAnyBox sends e-mails with a summary of accesses at that level.
To access encrypted information is necessary to enter the access code in a record. If the access code is temporarily remembered, user accesses all records without entering the access code..
Watching of accesses and/or changes is inheritable – if user watches changes in Safe Box Group, all Safe Boxes, and records within the Safe Box Group will inherit watching of changes/accesses from the parent level.
From the root level is possible to edit watching for all currently accessible Safe Box Groups, Safe Boxes, and records by clicking the Watching... button.
Watching of changes/accesses for Safe Box Groups, Safe Boxes, and records that you create or to which you obtain access in the future depends on the user’s settings of automatic watching.

In the Watching report , it is possible to check what the currently logged user is watching.
Changes in all Safe Box Groups, Safe Boxes, and records within them, which you can currently access, will be watched.
Watching of changes will be explicitly set for all currently accessible Safe Box Groups and Safe Boxes. Records inherit watching of changes from the Safe Box in which they are stored.
Note: Watching of changes for Safe Box Groups, Safe Boxes, and records that you create or to which you obtain access in the future depends on user’s settings and whether the level in which will be stored watches accesses, because watching of accesses may be inherited from the parent level.
After clicking the Start watching changes to everything button, it is necessary to confirm dialog window.
Accesses to encrypted information in the records stored in all Safe Boxes and Safe Box Groups to which you have access currently will be watched.
Watching of accesses will be explicitly set for all currently accessible Safe Box Groups and Safe Boxes. Records inherit the watching of accesses from the Safe Box in which they are stored.
Note: Watching of accesses for Safe Box Groups, Safe Boxes, and records that you create or to which you obtain access in the future depends on user’s settings and whether the level in which will be stored watches accesses, because watching of accesses may be inherited from the parent level.
After clicking the Start watching accesses to everything button, it is necessary to confirm dialog window.
Changes in all Safe Box Groups, Safe Boxes, and records within them,
which you can access currently will no longer be watched.
Watching of changes can reactivated at any time.
Note: Watching of changes for Safe Box Groups, Safe Boxes, and records that you create or to which you obtain access in the future depends on the user’s settings of automatic watching.
After clicking the Stop watching changes to everything button, it is necessary to confirm dialog window.
Access to encrypted information in all Safe Box Groups, Safe Boxes, and records within them which you can access currently will no longer be watched.
Watching of accesses can reactivated at any time.
Note: Watching of accesses for Safe Box Groups, Safe Boxes, and records that you create or to which you obtain access in the future depends on the user’s settings of automatic watching.
After clicking the Stop watching accesses to everything button, it is necessary to confirm dialog window.
After clicking Stop watching all button, the watching of changes and accesses will be deactivated for all currently accessible Safe Box Groups and Safe Boxes, and records.
Watching of accesses and/or changes can reactivated at any time.
Note: Watching of accesses for Safe Box Groups, Safe Boxes, and records that you create or to which you obtain access in the future depends on the user’s settings of automatic watching.
After clicking the Stop watching all button, it is necessary to confirm dialog window.
Create Edit Watching... Delete
Safe Box Group is intended for associating Safe Boxes into larger units. For example, the Safe Box Group can associate all Safe Boxes related to some project, server and so on.
Access rights can be managed for each Safe Box Group separately. For Safe Box Groups, which are not private, is applied the dynamic inheritance of access rights. The inheritance permission can be set for root level or Safe Box Group. When a user has the inheritance permission for Safe Box Group, all new shared Safe Boxes inside this group will inherit his permissions from Safe Box Group.
If the user has set Inherited permission for the root level, he automatically inherits permissions for all shared Safe Box Groups and Safe Boxes within the range of the user’s domain.
When the Safe Box Group is private, the inheritance of access rights is blocked. However, the permissions to the private Safe Box Group can be assigned manually.
To create a Safe Box Group, the user needs to have assigned the Create permission for the root level.
To create a Safe Box Group click the New Safe Box Group button. In the Safe Box Group, it is necessary to set a name, a password pattern and a type (private or shared). Into a Safe Box Group can be created a new Safe Box or can be moved existing Safe Box.

If the Safe Box Group is private, all Safe Boxes in it are also considered private.
Safe Box Group name should characterize its content to work with SecureAnyBox more effectively and conveniently. Each name must be unique within the range of root level.
However, a user can create two Safe Box Groups with the same name, if one of the Safe Box Groups is private. The name of a private Safe Box Group is stored along with a username of its owner, so both names are unique.
The description should more precisely characterize the Safe Box Group for better distinction from others.
The default password pattern that is automatically preset in all Safe Boxes and records within the range of Safe Box Group.
Each letter in the pattern corresponds to a letter in the generated password.
See examples of the password pattern
Characters allowed in the password pattern and their meaning:
v – lowercase vowel a,e,i,o,u,y
V – mixed case vowel (A,E,I,O,U,Y,a,e,i,o,u,y)
Z – upper case vowel
c – lowercase consonant (b,c,d,f,g,h,j,k,l,m,n,p,q,r,s,t,v,w,x,z)
C – mixed case consonant
z – upper case consonant
l - any alphabet character (vowel or consonant) - lowercase
A - any alphabet character - mixed case
u – upper case alphabet
d - digit (0-9)
s – special character (.,@,&,*,(,),<,>,_,],[,%,$,#,\,/,?,;,-,:)
n – digit or special character
\ - escape character - next character is used as is (e.g.,pattern ‘\-‘ outputs ‘-‘ in the resulting password)
* - any allowed character
Default pattern is CVCVdddCVCCVdC (this might generate passwords such as: wEHe063heFme4p).
For example, you can set password pattern as ‘\p\a\s\sddddddd‘ and this might generate passwords such as ‘pass1762885‘ or ‘pass5687412‘.
Enter an external files path that will be preset to all Safe Boxes within the Safe Box Group.
The path should be specified in MS Windows format (e.g. L:\SAB_DRIVE). If an external file path is changed, SecureAnyBox will store all new external files at the new location, but all previously stored files will remain at their original location.
Without
SAB Launcher or
SecureAnyBox plugin for Total Commander it is not possible to add external files to SecureAnyBox or work with them.
Safe Box Group type is important for the dynamic inheritance of access rights.
When the Safe Box Group is private, none of the permissions will be inherited from a parent level. However, access rights to the private Safe Box Group can be assigned manually.
If the Safe Box Group is shared, the dynamic inheritance of access rights will be applied.
If the value is read-only (plain text), the user does not have permission to Modify a Safe Box Group type and create private Safe Box Groups.
Private – Blocks access rights inherited from parent level.
p(hide#safebox.SAFEBOX_GROUP.shared.note). Shared – Access rights are inherited from parent level.
To be able to edit the Safe Box Group, a user must have permission to Modify.
For each of Safe Box Groups, it is possible to change name, description, password pattern, external files path and Safe Box Group Type.
If an external file path is changed, SecureAnyBox will store all new external files at the new location, but all previously stored files will remain at their original location.
For each Safe Box Group, you can turn on two types of watching – watching changes, and watching accesses to encrypted information. In a case that someone changed the watched Safe Box Group, or Safe Box, or record within these Safe Boxes, or someone accessed encrypted information in the record within these Safe Boxes, an e-mail notification is sent to a user who watches the Safe Box Group (depending on the configuration of mail notifications).
To access encrypted information is necessary to enter the access code in a record. If the access code is temporarily remembered, user accesses all records without entering the access code.
The user can customize the notification settings in user preferences.
Watching of changes for Safe Box Groups, Safe Boxes, and records that you create or to which you obtain access in the future depends on the user’s settings of automatic watching.
To set watching for the Safe Box Group, click the Watching... button, watching menu will display.

In the
Watching report
is possible to check what the currently logged user is watching within the Safe Box Group.
Current status of watching for the Safe Box Group is displayed next to the
Watching...
button.
|
|
Watching of changes and accesses to encrypted data is set explicitly for the Safe Box Group. |
|
|
Watching of changes is set for the Safe Box Group. Watching of accesses to encrypted data not set. |
|
|
Watching of changes not set. Watching of accesses to encrypted data is set explicitly for the Safe Box Group. |
Safe Box Groups can have watching of accesses and/or changes set explicitly only.
By checking fields Watching Changes , or Watching Accesses , user immediately set explicit watching of changes/accesses for the Safe Box Group. All Safe Boxes within this Safe Box Group, and records in them, will inherit the watching of changes/accesses from the Safe Box Group.
All Safe Boxes currently stored in this Safe Box Group will have set the watching of changes explicitly, and changes in them will remain watched even if these Safe Boxes are moved to another Safe Box Group where changes are not watched.
Records stored in Safe Boxes within this Safe Box Group will inherit watching of changes from the Safe Box.
Note: If the automatic watching of changes not set, Safe Boxes (and records in them) added into this Safe Box Group in the future will inherit watching of changes from the Safe Box Group. Otherwise, all Safe Boxes and records will have set the watching of changes explicitly.
After clicking the Start watching changes within this Safe Box Group button, it is necessary to confirm dialog window.
All Safe Boxes currently stored in this Safe Box Group will have set the watching of accesses explicitly, and accesses to encrypted information in them will remain watched even if these Safe Boxes are moved to another Safe Box Group where accesses are not watched.
Records stored in Safe Boxes within this Safe Box Group will inherit watching of accesses from the Safe Box.
Note: If the automatic watching of accesses not set, Safe Boxes (and records in them) added into this Safe Box Group in the future will inherit watching of accesses from the Safe Box Group. Otherwise, all Safe Boxes, and records will have set the watching of accesses explicitly.
After clicking the Start watching accesses within this Safe Box Group button, it is necessary to confirm dialog window.
Safe Box Group, all Safe Boxes within this Safe Box Group, and all records in them will no longer have set the watching of changes.
Watching of changes can reactivated at any time.
Note: Watching of changes for Safe Boxes, and records within this Safe Box Group that you create or to which you obtain access in the future depends on the user’s settings of automatic watching.
After clicking the Stop watching changes within this Safe Box Group button, it is necessary to confirm dialog window.
Safe Box Group, all Safe Boxes within this Safe Box Group, and all records in them will no longer have set the watching of accesses to encrypted data.
Watching of accesses can reactivated at any time.
Note: Watching of accesses for Safe Boxes, and records within this Safe Box Group that you create or to which you obtain access in the future depends on the user’s settings of automatic watching.
After clicking the Stop watching accesses within this Safe Box Group button, it is necessary to confirm dialog window.
Safe Box Group can be deleted from the root level. To be able to delete the Safe Box Group, a user must have permission
Delete. If a user has this permission, a cross icon (
![]() ) is displayed at the end of a row.
) is displayed at the end of a row.
After clicking on a cross icon, a user is asked to confirm deleting of the Safe Box Group. When confirmed, the Safe Box Group is deleted and is no longer displayed.
Deleted Safe Box Group user can immediately restore by clicking on the Undo in the displayed message.

Create Edit Move Import records Watching... Connect from Safe Box Delete
Safe Boxes are intended for storing records. Different types of records - accounts, secret accounts, files, certificates, credit cards - can be stored inside a Safe Box.
Access rights can be managed for each Safe Box separately. For Safe Boxes, which are not private, is applied the dynamic inheritance of access rights. The inheritance permission can be set for root level or Safe Box Group. When a user has this permission, all new shared Safe Boxes will inherit his permissions from parent level.
When the Safe Box is private, the inheritance of access rights is blocked. However, the access rights to the private Safe Box can be assigned manually.
To be able to create a Safe Box, a user must have permissions to Create for the root level or a Safe Box Group in which the Safe Box will be created.
New Safe Box can be created at the root level or inside a Safe Box Group by clicking on the
New Safe Box
button. In the Safe Box, it is necessary to set a name, a password pattern and a type (private or shared). Private Safe Box can be created only at the root level.
When creating a Safe Box into a Safe Box Group the Safe Box Type cannot be set – is given by Safe Box Group Type.

Safe Box name should characterize its content to work with SecureAnyBox more effectively and conveniently. Each name must be unique within the range of a Safe Box Group or the root level.
However, a user can create two Safe Boxes with the same name at the root level, if one of the Safe Boxes is private. The name of a private Safe Box is stored along with a username of its owner, so both names are unique.
The description should more precisely characterize the Safe Box for better distinction from others.
The default password pattern that is automatically preset in all records within the range of Safe Box.
Each letter in the pattern corresponds to a letter in the generated password.
See examples of the password pattern
Characters allowed in the password pattern and their meaning:
v – lowercase vowel a,e,i,o,u,y
V – mixed case vowel (A,E,I,O,U,Y,a,e,i,o,u,y)
Z – upper case vowel
c – lowercase consonant (b,c,d,f,g,h,j,k,l,m,n,p,q,r,s,t,v,w,x,z)
C – mixed case consonant
z – upper case consonant
l - any alphabet character (vowel or consonant) - lowercase
A - any alphabet character - mixed case
u – upper case alphabet
d - digit (0-9)
s – special character (.,@,&,*,(,),<,>,_,],[,%,$,#,\,/,?,;,-,:)
n – digit or special character
\ - escape character - next character is used as is (e.g.,pattern ‘\-‘ outputs ‘-‘ in the resulting password)
* - any allowed character
Default pattern is CVCVdddCVCCVdC (this might generate passwords such as: wEHe063heFme4p).
For example, you can set a password pattern as ‘\p\a\s\sddddddd‘ and this might generate passwords such as ‘pass1762885‘ or ‘pass5687412‘.
Enter an external files path that will be used as a location to store external within the Safe Box.
The path should be specified in MS Windows format (e.g. L:\SAB_DRIVE). If an external file path is changed, SecureAnyBox will store all new external files at the new location, but all previously stored files will remain at their original location.
Without
SAB Launcher or
SecureAnyBox plugin for Total Commander it is not possible to add external files to SecureAnyBox or work with them.
Safe Box type is important for the dynamic inheritance of access rights.
When the Safe Box is private, none of the permissions will be inherited from a parent level. However, access rights to the private Safe Box can be assigned manually.
If the Safe Box is shared, the dynamic inheritance of access rights will be applied.
If the value is read-only (plain text), the user does not have permission to change a Safe Box type.
The Safe Box type cannot be set to Safe Boxes inside a Safe Box Group – for these Safe Boxes is given by the Safe Box Group type.
Private – Blocks access rights inherited from parent level.
To be able to edit the Safe Box, a user must have permission to Modify.
For each of Safe Boxes, it is possible to change name, description, password pattern, external files path and Safe Box Type.
If an external file path is changed, SecureAnyBox will store all new external files at the new location, but all previously stored files will remain at their original location.
If the Safe Box is not in a Safe Box Group, it is possible to change a Safe Box type also.
To be able to move the Safe Box, a user must have permission to Delete. When moving, the Safe Box is effectively deleted from an original location and created at a target location.
To move the Safe Box click the button Move Safe Box , and wait until is displayed a list of possibilities, to where it is possible to move the Safe Box.

Click on a row in a list select the destination into which the Safe Box will be moved and confirm the move by entering the access code. Have you forgotten the access code?
By moving the Safe Box, you may change permissions of other users for the Safe Box.
Into the Safe Box can be imported records from other applications. Before importing, please create target Safe Box. On the Safe Box page, then click the Import... button and in the displayed menu select SecureAnyBox Importer

Import utilities can be downloaded from Downloads page too.
After clicking, a dialog with a download link displays. When downloaded, extract files from the zip archive and run a utility.

In the SecureAnyBox Importer, the user needs to enter SAB address to the appropriate field. You can get and copy SAB address by clicking the Copy SAB address option in the menu, that displays after clicking on the Import... button.

For each Safe Box, you can turn on two types of watching – watching changes and watching accesses to encrypted information. In a case that someone changed the watched Safe Box or record within the Safe Box or someone accessed encrypted information in the record within the Safe Box, an e-mail notification is sent to a user who watches the record (depending on the configuration of mail notifications).
If the Safe Box is watched, all records in it are watched also. The user can customize the notification settings in user preferences.
Watching of changes for Safe Box Groups, Safe Boxes, and records that you create or to which you obtain access in the future depends on the user’s settings of automatic watching.

In the
Watching report
is possible to check what the currently logged user is watching within the Safe Box.
Current status of watching for the Safe Box is displayed next to the
Watching...
button.
|
|
Watching of changes is set explicitly for the Safe Box. Accesses are not watched. |
|
|
Watching of changes is inherited from the parent level. Accesses are not watched. |
|
|
Watching of accesses to encrypted data is set explicitly for the Safe Box. Changes are not watched. |
|
|
Watching of accesses to encrypted data is inherited from the parent level. Changes are not watched. |
|
|
Watching of changes and accesses to encrypted data is set explicitly for the Safe Box. |
|
|
Watching of changes is set explicitly for the Safe Box. Watching of accesses to encrypted data is inherited from the parent level. |
|
|
Watching of changes is inherited from the parent level. Watching of accesses to encrypted data is set explicitly for the Safe Box. |
|
|
Watching of changes and accesses to encrypted data is inherited from the parent level. |
By checking fields Watching Changes , or Watching Accesses , user immediately set explicit watching of changes/accesses for the Safe Box. All records within this Safe Box will inherit the watching of changes/accesses from the Safe Box.
All records currently stored in this Safe Box will have set the watching of changes explicitly and the changes will be watched even if record moved to another Safe Box that where the changes are not watched.
Note: If the automatic watching of changes not set, records added into this Safe Box in the future will inherit watching of changes from the Safe Box. Otherwise, all records will have set the watching of changes explicitly.
After clicking the Start watching changes within this Safe Box button, it is necessary to confirm dialog window.
All records currently stored in this Safe Box will have set the watching of accesses explicitly and the accesses to encrypted information will be watched even if record moved to another Safe Box where the accesses are not watched.
Note: If the automatic watching of changes not set, records added into this Safe Box in the future will inherit watching of changes from the Safe Box. Otherwise, all records will have set the watching of changes explicitly.
After clicking the Start watching accesses within this Safe Box button, it is necessary to confirm dialog window.
Changes in this Safe Box and all records within it will no longer be watched.
Note: If the Safe Box is stored in Safe Box Group, then Safe Box (and records within it) may have inherited watching of changes from the Safe Box Group.
Watching of changes for records within this Safe Box
that you create or to which you obtain access in the future depends on the user’s settings of automatic watching.
After clicking the Stop watching changes within this Safe Box button, it is necessary to confirm dialog window.
Accesses to encrypted information in this Safe Box and all records within it will no longer be watched.
Watching of changes can be reactivated anytime.
Note: If the Safe Box is stored in Safe Box Group, then Safe Box (and records within it) may have inherited watching of accesses from the Safe Box Group.
Watching of changes for records within this Safe Box that you create or to which you obtain accesses in the future depends on the user’s settings of automatic watching.
After clicking the Stop watching accesses within this Safe Box button, it is necessary to confirm dialog window.
If any account or secret account stored in Safe Box has defined connection type, it is possible to open the connection by click on the Connect button. To open connection is necessary to have installed SecureAnyBox Launcher on your station.

If username (login) and password stored in the record, the user automatically connects to the target (server, station, etc.).
To be able to delete the Safe Box, a user must have permission to
Delete. If a user has this permission, a cross icon (
![]() ) is displayed at the end of a row.
) is displayed at the end of a row.
Safe Box can be deleted from the Safe Box Group page or the root level page. To delete Safe Box, please click the cross icon at the end of a row. After clicking on a cross icon, a user is asked to confirm deleting of the Safe Box. When confirmed, the Safe Box is deleted and is no longer displayed.

Deleted Safe Box user can immediately restore by clicking on the Undo in the displayed message.
Create Edit Change password Password History Copy as... Watching... Connect Move Move to White Envelope Delete
Records are stored inside the Safe Boxes and are intended to store important information. By the nature of the information that will store, a user needs to select a type of record. All types of records and which information can be stored in them, are listed in the table below.
| Record type | Field | |||||||||||||||||||
| Name | Description | Tags | Note | Password pattern | Address | Login Site | Login | Connection Type | Connection Options | Secret Note | Password | File | Alias | Certificate | Certificate password | Number | Expiration Date | CVV | PIN | |
| Account | ||||||||||||||||||||
| Secret Account | ||||||||||||||||||||
| File | ||||||||||||||||||||
| Certificate | ||||||||||||||||||||
| Credit Card | ||||||||||||||||||||
|
|
Information can be stored in this record type. Access to this information is not audited. |
|
|
Information can be stored for this type of record. This information will be encrypted when the record is saved. You need to enter an access code to access it. Access to this information is audited. |
|
|
Information cannot be stored in this record type. |
To be able to create a record, the user must have permission to Create for the Safe Box, into which the record will create.
At the page of Safe Box into which a record should create, click on the
Add...
button, and in the context menu, select a type of record. After that, a form for creating a new record will display.
When creating the record, it is necessary to set a name. Other fields are optional. All values can be modified later.

The account name should characterize the purpose of stored data to work more effectively and conveniently.
Each name must be unique inside a single Safe Box.
The account name can be modified later.
Maximum length: 255 characters
Address, link or description where the information stored in the account used.
When the address stored in a correct format (e.g.,“https://192.168.1.231”), it will appear as a link. For a location in a local network, you can use an IP address (e.g. “http://172.22.60.30”), for other webs, e-shops, etc. you can use a URL address (e.g.,“http://www.ebay.com”).
Addresses can be also stored in other formats like an SSH (e.g.,“ssh://admin@myserver.com”), FTP (e.g., “ftp://myserver.com”) and so on.
In the address field, it is possible to store a hostname, an IP address and is even possible to store a port. The port has to be separated from the host by a colon. (e.g. “172.22.88.75:8876” or “test.tdp.cz:887”).
The address is an optional value.
Maximum length: 1000 characters
e.g., URL, hostname or IP address of the server where you use the stored password.
The login site is used for better specification where the stored account can be used. The value of this field is used especially in the browser extension to edit the visibility of an account.
For example, the stored account will be used to login to Gmail. If the Address field is set to URL “https://accounts.google.com”, and the Login Site field is set to “google.com”, then the account will be visible in browser extension for all google login forms, even if the actual URL will differ from "https://accounts.google.com."
Maximum length: 1000 characters
The username that you use to log in.
Maximum length: 255 characters
The description should more specifically characterize an account.
In the description can be stored only one line of a text. A longer description can be stored as the note.
Maximum length: 2000 characters
Maximum length of one tag: 32 characters
Default password pattern for Accounts where no password pattern is set.
Each letter in the pattern corresponds to letter in the generated password.
See examples of the password pattern
Characters allowed in the password pattern and their meaning:
v – lowercase vowel a,e,i,o,u,y
V – mixed case vowel (A,E,I,O,U,Y,a,e,i,o,u,y)
Z – upper case vowel
c – lowercase consonant (b,c,d,f,g,h,j,k,l,m,n,p,q,r,s,t,v,w,x,z)
C – mixed case consonant
z – upper case consonant
l - any alphabet character (vowel or consonant) - lowercase
A - any alphabet character - mixed case
u – upper case alphabet
d - digit (0-9)
s – special character (.,@,&,*,(,),<,>,_,],[,%,$,#,\,/,?,;,-,:)
n – digit or special character
\ - escape character - next character is used as is (e.g., pattern ‘\-‘ outputs ‘-‘ in the resulting password)
* - any allowed character
Default pattern is CVCVdddCVCCVdC (this might generate passwords such as: wEHe063heFme4p).
For example, you can set password pattern as ‘\p\a\s\sddddddd‘ and this might generate password such as ‘pass1762885‘ or ‘pass5687412‘.
Maximum length: 255 characters
The note field is intended for multiline information about the account. For example, as the note can be stored a description of the account, a list of steps how to successfully log in, a description of the configuration and so on.
Maximum length: 4000 characters
Please select connection type. If the SecureAnyBox Launcher installed, is possible to open connection directly from the account page. To create a connection, SecureAnyBox Launcher needs to download from a secret account the values of Address and Login fields and the stored password.
In the address field is possible to store a hostname, an IP address and is even possible to store a port. The port has to be separated from the host by a colon. (e.g. “172.22.88.75:8876” or “test.tdp.cz:887”).
Maximum length: 2000 characters
The password you use to log in.
Into this field can be stored a password which you already have or you might generate a new one. The password can be generated by clicking on the
Generate password
button. Generated passwords are safer and don’t have any link to a person who made them (like a pet’s name, favorite actor or nickname).
Generated passwords are formatted in accordance with the current password pattern. Generated passwords can be edited.
While editing the password, you can see how long your password is, how many lowercase letters, uppercase letters, numbers or other symbols password contains and how secure your password is.
After saving an account record, the password will be encrypted. The password can be decrypted after entering the access code only.
Maximum length: 255 characters

number of characters
number of lowercase letters
number of uppercase letters
number of digits
number of special characters
pointer how secure the password is
button for displaying the password
time to crack password offline
password entropy (the higher the better)

The secret account name should characterize the purpose of stored data to work more effectively and conveniently.
Each name must be unique inside a single Safe Box.
The secret account name can be modified later.
Maximum length: 255 characters
The login site is used for better specification where the stored account can be used. The value of this field is used especially in the browser extension to edit the visibility of an account.
For example, the stored account will be used to login to Gmail. If the Address field is set to URL “https://accounts.google.com”, and the Login Site field is set to “google.com”, then the account will be visible in browser extension for all google login forms, even if the actual URL will differ from "https://accounts.google.com."
Maximum length: 1000 characters
The description should more specifically characterize a secret account.
In the description can be stored only one line of a text. A longer text is possible to store as the note.
Maximum length: 2000 characters
Maximum length of one tag: 32 characters
Password pattern used when generating the password for the secret account.
Each letter in the pattern corresponds to a letter in the generated password.
See examples of the password pattern
Characters allowed in the password pattern and their meaning:
v – lowercase vowel a,e,i,o,u,y
V – mixed case vowel (A,E,I,O,U,Y,a,e,i,o,u,y)
Z – upper case vowel
c – lowercase consonant (b,c,d,f,g,h,j,k,l,m,n,p,q,r,s,t,v,w,x,z)
C – mixed case consonant
z – upper case consonant
l - any alphabet character (vowel or consonant) - lowercase
A - any alphabet character - mixed case
u – upper case alphabet
d - digit (0-9)
s – special character (.,@,&,*,(,),<,>,_,],[,%,$,#,\,/,?,;,-,:)
n – digit or special character
\ - escape character - next character is used as is (e.g., pattern ‘\-‘ outputs ‘-‘ in the resulting password)
* - any allowed character
Default pattern is CVCVdddCVCCVdC (this might generate passwords such as: wEHe063heFme4p).
For example, you can set a password pattern as ‘\p\a\s\sddddddd‘ and this might generate passwords such as ‘pass1762885‘ or ‘pass5687412‘.
Maximum length: 255 characters
This field intended for multiline information about the secret account. For example, as the note is possible to store a description of the secret account, a list of steps how to successfully log in, a description of the configuration and so on.
Maximum length: 4000 characters
Please select the connection type. If the SecureAnyBox Launcher installed, it is possible to open a connection directly from the secret account page.
To create a connection, SecureAnyBox Launcher needs to download from a secret account the values of Address and Login fields and the stored password.
In the address field is possible to store a hostname, an IP address and is even possible to store a port. The port has to be separated from the host by a colon (e.g. 172.22.88.75:8876 or test.tdp.cz:887).
Address, link or description where the information stored in the secret account used.
When the address stored in a correct format (e.g. “https://192.168.1.231”), it will appear as a link. For a location in a local network, you can use an IP address (e.g. “http://172.22.60.30”), for other webs, e-shops, etc. you can use a URL address (e.g., “http://www.ebay.com”).
Addresses can also be stored in other formats like an SSH (e.g., “ssh://admin@myserver.com”), FTP (e.g., “ftp://myserver.com”) and so on.
The address is an optional value.
In the address field is possible to store a hostname, an IP address and is even possible to store a port. The port has to be separated from the host by a colon. (e.g., 172.22.88.75:8876 or test.tdp.cz:887).
Unlike in an account, the address in a secret account will be encrypted. The address can be decrypted after entering the access code only.
Maximum length: 1000 characters
The username that you use to log in.
Unlike in an account, the login in a secret account will encrypt. The login can only be decrypted after entering the access code.
Maximum length: 255 characters
The secret note field intended for storing multiline information about the file. Unlike a note, the secret note will encrypt. The secret note can only be decrypted after entering the access code only.
Maximum length: 4000 characters
Maximum length: 2000 characters
The password you use to log in.
Into this field can be stored a password which you already have or you might generate a new one. The password can is possible to generate by clicking on the
Generate password
button. Generated passwords are safer and don’t have any link to a person who made them (like a pet’s name, favorite actor or nickname).
Generated passwords are formatted by the current password pattern. Generated passwords can also be edited.
While editing the password, you can see how long your password is, how many lowercase letters, uppercase letters, numbers or other symbols password contains and how secure your password is.
After saving a secret account record, the password will encrypt. The password can only be decrypted after entering the access code.
Maximum length: 255 characters

number of characters
number of lowercase letters
number of uppercase letters
number of digits
number of special characters
pointer how secure the password is
button for displaying the password
time to crack password offline
password entropy (the higher the better)

The file name should characterize the purpose of stored data to work more effectively and conveniently.
Each name must be unique inside a single Safe Box.
The file name can be modified later.
Maximum length: 255 characters
The description should more specifically characterize a file.
In the description can be stored only one line of a text. A longer description should store as the note.
Maximum length: 2000 characters
Maximum length of one tag: 32 characters
This field is intended for multiline information about the file. For example, as the note can be stored a description of the file, a list of steps how to use it and so on.
Maximum length: 4000 characters
Into this field can be selected a file, which will be stored in this file record. Select the file from your computer or server by clicking on the
Browse...
button.
After saving the record, the stored file will encrypt. The file can be decrypted after entering the access code only. After the file decrypted, it will be possible to download or change the file.
The secret note field is intended for multiline information about the file. Unlike a note, the secret note will encrypt. The secret note can only be decrypted after entering the access code.
Maximum length: 4000 characters

Certificate name should characterize the purpose of stored data to work more effectively and conveniently.
Each name must be unique inside a single Safe Box.
The certificate name can be modified later.
Maximum length: 255 characters
The description should more specifically characterize a certificate.
In the description can be stored only one line of a text. A longer description should store as the note.
Maximum length: 2000 characters
Maximum length of one tag: 32 characters
The note field is intended for multiline information about the certificate. For example, like the note, it is possible to store a description of the certificate, a list of steps how to use the certificate and so on.
Maximum length: 4000 characters
The alias is used as the name under which is the certificate file stored in the repository. After saving a certificate, the alias will encrypt. . The alias will be decrypted after entering the access code only.
Maximum length: 255 characters
Into this field can be selected a keystore file (a certificate, a public or a private key), which will store in this record. Select the file from your computer or server by clicking on the “Browse...” button.
After saving the record, the stored file will encrypt. The file can only be decrypted after entering the access code. After decrypting the file, it will be possible to download or change the file..
The password that is used with the certificate. The password can be generated by clicking on the
Generate password
button. Generated passwords are safer and don’t have any link to a person who made them (like a pet’s name, favorite actor or nickname).
Generated passwords are formatted by the current password pattern. Generated passwords can also be edited.
After saving a certificate record, the password will be encrypted. The password can be decrypted after entering the access code only.
Maximum length: 255 characters
The secret note field is intended for multiline information about the certificate. Unlike a note, the secret note will be encrypted. The secret note can be decrypted after entering the access code only.
Maximum length: 4000 characters

The name should characterize the credit card to work more effectively and conveniently. For example, as the name of the card can be used a name of the bank, the name of person or company which is the owner of a card, etc.
Each name must be unique inside a single Safe Box.
The credit card name can be modified later.
Maximum length: 255 characters
The description should more specifically characterize a credit card.
In the description can be stored only one line of a text. A longer description should be stored in the note field.
Maximum length: 2000 characters
Maximum length of one tag: 32 characters
The note field is intended for multiline information about the credit card. For example, as the note is possible to store a description of the credit card, the currency of a card, for which payments the card should be used and so on.
Maximum length: 4000 characters
Credit card number. After saving a record, the number will be encrypted. The number can be decrypted after entering the access code only.
Maximum length: 64 characters
The expiration date is the last day of the credit card validity. In case that expiration date on the card is in the format of MM/YY only, the card is valid until last day of the month (e.g., 03/16 means March 31st, 2016, 06/19 means June 30th, 2019 and so on).
After saving a record, the CVV code will encrypt. The CVV code can only be decrypted after entering the access code.
CVV code is usually listed at the back side of your card.
The code used when paying online with the credit card.
After saving a record, the CVV code will be encrypt. The CVV code can only be decrypted after entering the access code.
Storing the CVV code is optional.
Maximum length: 64 characters
PIN code of the credit card.
After saving a record, the PIN code will encrypt. The PIN code can only be decrypted after entering the access code.
Storing the PIN code is optional.
Maximum length: 64 characters
The secret note field is intended for multiline information about the credit card. Unlike a note, the secret note will be encrypted. The secret note can be decrypted after entering the access code only.
Maximum length: 4000 characters
To be able to edit the record, a user must have a Modify permission for a Safe Box in which the record is stored.
To modify an record, click the Edit button on a page of record. After clicking, an edit form displays. In the edit form, it is possible to change any value of record. To edit values in the Secured section of the form, is necessary to enter the access code first. Only passwords in account and secret account type of record have to be edited differently.
To edit account’s and secret account’s password, click the Change password button on a record’s page.
To be able to change the record’s password, a user must have a Modify permission for a Safe Box, in which the record is stored.
To change record’s password, click on the
Change password
button at record’s pag. After clicking, the form for entering a new password appears.
The password can be changed by entering a new password into fields or by generating a new one. Generated passwords are formatted by the current password pattern. Generated passwords are possible to edit.
Change of the record’s password has to be confirmed by entering the access code (unless the access code is cached). Have you forgotten the access code?
By clicking the Change password button, you can change passwords in an account and secret account type of record only. Certificate password can be changed in the edit form of certificate.
For each
account and
secret account is recorded a password history. The password history will display after clicking the
Password History
button at record’s page.
At the password history’s page, all of the record’s password changes display in a table.

After clicking on a row in a table and entering the access code, a user can view the password which was valid after that change. Have you forgotten the access code?
Each record can be copied, either as the same type of record or the different type of record. To make a copy, click the Copy as ... button and select the record type.

When making a copy of a record, the field values are copied to the new record – if it is possible to save such values in the selected record type. A copy of the record is created in the same Safe Box, so it is necessary to edit the name of the record.

After saving a copy of the record, the original record is displayed, and the newly created record can be accessed by clicking on the name of the new record in the displayed message.
For each record, you can turn on two types of watching – watching changes and watching accesses to encrypted information. In a case that someone changed the watched record or someone accessed encrypted information, an e-mail notification is sent to a user who watches the record (depending on the configuration of mail notifications).
The user can customize the notification settings in user preferences.

Watching settings are inheritable – if you watch changes in Safe Box Group, you also watch changes in all Safe Boxes within the Safe Box Group, as well as changes in records within all Safe Boxes.
Whether the watching is set explicitly for a specific record or inherited from the parent level can be recognized by the icon color which is displayed next to the
Watching...
button.
|
|
Watching of changes is set explicitly for the record. Accesses are not watched. |
|
|
Watching of changes is inherited from the parent level. Accesses are not watched. |
|
|
Watching of accesses to encrypted data is set explicitly for the record. Changes are not watched. |
|
|
Watching of accesses to encrypted data is inherited from the parent level. Changes are not watched. |
|
|
Watching of changes and accesses to encrypted data is set explicitly for the record. |
|
|
Watching of changes is set explicitly for the record. Watching of accesses to encrypted data is inherited from the parent level. |
|
|
Watching of changes is inherited from the parent level. Watching of accesses to encrypted data is set explicitly for the record. |
|
|
Watching of changes and accesses to encrypted data is inherited from the parent level. |
By checking fields Watching Changes , or Watching Accesses , user immediately set explicit watching of changes/accesses for the record.
If the record (account and secret account only) has specified a connection type, it is possible to open the connection by click on the Connect button. To open connection is necessary to have installed SecureAnyBox Launcher on your station.

If username (login) and password is stored in the record, the user connects to the target (server, station, etc.) automatically.
To be able to move the record, a user must have a Delete permission for the Safe Box in which the record stored and Create permission for the Safe Box into which the record will move. When moving, the record will be effectively deleted from the original Safe Box and created in the target Safe Box.
To move the record, click on the Move record button. After clicking, a list of possibilities to where it is possible to move the record displays.

In the list, the name of the Safe Box Group is blue, and after clicking it, a list of Safe Boxes stored in the Safe Box Group displays. If you want to move from a Safe Box Group to the root level, click on the first line with two dots.
The names of the Safe Boxes are black and by click on them a user to select the Safe Box to which the record will be moved. Moving of the record have to be confirmed by entering an access code. Have you forgotten the access code?
All record permissions are determined by the Safe Box permissions in which the record stored. By moving the record, you may change even yours permissions, and you will not be able to return the record to the original Safe Box.
This option is available only if currently logged user has activated White Envelope. More about White Envelopes...
To be able to move the record into a White Envelope, a user must have a Delete permissions for Safe Box in which the record stored. When moving, the record will be effectively deleted from the original Safe Box and created in the White Envelope.
To move the record into a White Envelope, click on the appropriate button.
Before moving the record into a White Envelope, the user is asked to confirm moving the record, by entering the access code. Have you forgotten the access code?
Moving the record into a White Envelope cannot be taken back.
To be able to delete the record, a user must have a
Delete permissions for Safe Box in which the record stored. If the user has this permission, a cross icon (
![]() ) is displayed at the specific record (at the end of the row).
) is displayed at the specific record (at the end of the row).
Record can be deleted from the Safe Box page. To delete the record, click the cross icon at the end of a row. After clicking on a cross icon, a user is asked to confirm deleting of the record. When confirmed, the record is deleted and is no longer displayed.

Deleted record user can immediately restore by clicking on the Undo in the displayed message.

At the Search page, a user can search stored records (such as Safe Boxes, Safe Box Groups, Accounts, etc.), by their name, specified tag of a field value. However, it is not possible to search record by a field value which is encrypted.
To initiate the search, start typing into a search field.

Activate White Envelope Security Officers page Open White Envelope Close White Envelope Editing Mode of White Envelopes Recover White Envelope Reactivate White Envelope Initialize Security Officers Possible situations
White Envelope is a special type of Safe Box, which is intended to store important information for which the access must not lose. If the user who stored data in the White Envelope is unavailable, Security Officers can access this information.
The White Envelope can store the same records as any other Safe Box – accounts, files, etc.
There are two ways to add records to White Envelopes – by creating new records in the White Envelope or by moving existing records from other Safe Boxes.
Users can change stored records, but cannot delete them.
Security Officers can delete White Envelopes and the records in them, by enabling editing mode.
To be able to use the White Envelopes, it is needed to set at least a minimum count of Security Officers.
The Security Officer is a special type of user’s role. To set Security Officers, go to the Users management and in the user details form, to add the role.
Minimum count of Security Officers depends on settings in the SecureAnyBox configuration and settings in a domain. Please check how many Security Officers are needed.
After Security officers set, it is possible to activate the White Envelope.
Only if a minimum count of Security Officers set, it is possible to activate the White Envelope. To activate the White Envelope, open a context menu by clicking on the arrow next to the user’s name in the top right corner of the page and click on the Activate White Envelope button.


For each of White Envelopes is possible to display which Security Officers who have access to it. To display Security Officers with access to the White Envelope, click the Security Officers button at the White Envelope page.

At the Security Officers page, you can see which Security Officers has access to the White Envelope and their e-mail. Above the table of Security Officers, is displayed a number of Security Officers needed to work together to perform actions with White Envelopes.
It is possible to filter displayed Security Officers, by entering a part of their name into the Filter field.

Only users with a role Security Officer can open White Envelopes of other users.
Should you need view encrypted values of records in another user’s White Envelope, open the White Envelope. To open the White Envelope, minimum count (two by default) of the Security Officers have to enter their access code.
Minimum count of Security Officers depends on settings in the SecureAnyBox configuration and settings in a domain. Please check how many Security Officers are needed.

In an opened White Envelope the Security Officers can view even encrypted values of records such as passwords, files, secret notes and so on.
Once the Security Officers finish their work with records in open White Envelope, they should close it. Security Officers can open and close the White Envelope repeatedly.

Security Officers can enable editing mode and delete White Envelopes or records in them. To enable the editing mode, two of the Security Officers have to enter their access code.
Minimum count of Security Officers depends on settings in the SecureAnyBox configuration and settings in a domain. Please check how many Security Officers are needed.

When editing mode enabled, into tables of White Envelopes or records is added the first column with checkboxes. The Security Officer selects which White Envelopes or records will delete by checking appropriate row in a table. After all White Envelopes or records to delete selected, click the Delete selected button.

Deleted White Envelopes and records from them cannot be restored.
Once the Security Officers finish their editing of White Envelopes, editing mode should be disabled. To disable editing mode, click on the appropriate button.

After the user with an active White Envelope resets access code, the White Envelope needs to recover. Until the White Envelope recovered, the user cannot view or change stored records and move records from other Safe Boxes into the White Envelope.
A White Envelope can be restored by a minimum count of the Security Officers.

If the count of Security Officers was below the minimum and new Security Officers added, to work with the White Envelopes, their owners have to reactivate them.
To reactivate the White Envelope, go to the White Envelope page and confirm a warning message. When message confirmed, enter the access code. After the access code entered, the White Envelope successfully reactivated.

For initialization of Security Officers, are two reasons – a user became the new Security Officer, or current Security Officer resets his access code.
Only two other Security Officers can initialize a Security Officer. To initialize Security Officers, click on the
Initialize Security Officers
button. After that, two of the Security Officers have to enter their access code.

After successful initialization, the Secure Officer has access to White envelopes of other users and may do all operations with White Envelopes as others Security Officers (open, close or recover White Envelope, or initialize Security Officer).
If any Security Officer deleted and count of Security Officers is not sufficient (below the threshold – set in a domain), it is necessary to add new Security Officers. After new Security Officers added, current Security Officers, need to initialize the new ones, to share the White Envelope key parts.

If any Security Officer deleted and count of Security Officers is below the minimum (set in a domain), it is necessary to set a new Security Officers.
All White Envelopes have been reset. Reactivating them is necessary..

If some Security Officer has been deleted and then re-added, it is necessary to set him as a Security Officer again. After the user has Security Officer role set, can be initialized.
At the Downloads page, you can download SAB Importer, SAB Launcher, web extensions, SAB Manager plugins for FAR and Total Commander, and a trial version of CBT client.

SecureAnyBox Importer is a utility intended to import records from CSV files and KeePass. From KeePass, it is possible to import records from kdb, kdbx, and xml files.

When importing records from CSV file, it is necessary to map account fields to columns in CSV file. After CSV file is selected, the Field map displays. When the mapping of columns to appropriate fields finished, it is possible to save a map for later usage.

When importing records from KeePass, it is possible to choose a record type, and view record values by double-clicking a record row in the Import preview.

p(#SABImporterParagraph3).After clicking the Import button, it is necessary to login to SecureAnyBox server (and enter 2FA code if required), enter the access code, and select Safe Box into which records will import. After import performed, report of import displays.

SecureAnyBox Launcher is a MS Windows application. In Safe Boxes is intended to be used to connect from (secret) accounts and for communication between web extensions and SecureAnyBox server
SecureAnyBox Launcher is an MS Windows (.NET Framework 4.5.2 or higher required) application delivered as a msi package. After installation, the application runs in the system tray and registers the custom URI scheme for sab:// links from the SecureAnyBox web interface.
In the SecureAnyBox account or secret account, you can set the connection type (RDP/SSH/SCP/SFTP/TELNET/WINBOX/RASDIAL). After clicking the
Connect
button at the (secret) account page, where the connection type set, web browser passes custom URI (sab://) to SecureAnyBox launcher.
Depending on the URI value, SecureAnyBox Launcher selects appropriate plugin (currently PuTTY for SSH, WinSCP for SCP/SFTP, MikroTik Winbox for WINBOX, and Remote Desktop for RDP). Then SecureAnyBox Launcher downloads account data using a one-time token that was received in the URI and started selected plugin.
To create a connection, SecureAnyBox Launcher needs to download from an account the values of Address and Login fields and the stored password.
In the address field is possible to store a hostname, an IP address and is even possible to store a port. The port has to be separated from the host by a colon. (e.g., "172.22.88.75:8876" or "test.tdp.cz:887").
The location of the WinSCP, MikroTik Winbox, and the PuTTY is detected automatically in Program Files but can be set manually in the SecureAnyBox Launcher settings. To open SecureAnyBox Launcher settings, click left mouse button on the SecureAnyBox Launcher icon in the system tray and in displayed context menu click Settings.

In the SecureAnyBox Launcher Settings, you can edit settings for Web extensions, change the location of WinSCP, MikroTik WinBox, and PuTTY or set size of Remote Desktop window, and influence settings of clipboard or printers.

If the SecureAnyBox server uses an SSL certificate that is not trusted in Windows, when Launcher connects to the server, a warning window will be displayed to warning about the potential security risk. This could be because the certificate is signed by a non-trusted certification authority in Windows, or because it is self-signed.

Please check with your administrator first to verify if the certificate is valid (e.g., a self-signed certificate). If so, you can accept it and approve the exception by clicking I have verified that this is a valid certificate button and then the Accept button. If you do not want this warning to appear again, you can permanently approve the exception by selecting the Accept this certificate permanently checkbox.
If this warning suddenly appears, and you have used Launcher before, it is very likely a security incident. In this case, do not approve the exception and contact your administrator!
Previously accepted exceptions can be reset in the Launcher settings in the Web Extension section, by clicking the Reset certificate exceptions button. It will remove only exceptions accepted in SAB Launcher. Other exceptions for certificates that you may have approved on your system or browsers will remain.
Part of SecureAnyBox Launcher configuration can be enforced by setting it in the Windows registry (HKLM).
When starting SecureAnyBox Launcher, settings are loaded first from the Launcher and then from the Windows registry – HKLM. The setting values are overwritten as they load, and the last loaded setting is used.
In Windows registry, it is possible to store all Web extension settings and RDP gateway.
Launcher settings keys are stored in
HKEY_LOCAL_MACHINE\SOFTWARE\TDP\SecureAnyBox Launcher. For a list of keys and recommended values, download the README file.
Click to download Launcher configuration enforced by Windows registry README file
You can also download a registry example file and edit key values in the file. After the file is edited, run it.
Click to download the Windows registry example file
SAB browser extensions simplify logging in to accounts on websites using stored accounts in SecureAnyBox.
If the extension on the web page recognizes the login fields, it will offer the user to fill in credentials from one of the saved accounts in SecureAnyBox. Also, the extension allows users to create accounts with login information directly from the website where they will be used.
Browser extension communicates with the SecureAnyBox Launcher, which communicates with the SecureAnyBox server, so to be able to work with browser extensions, it is necessary to have SecureAnyBox Launcher (minimum version 2.0.0.x) installed as well.
Download Firefox extension to your computer and drag and drop it to Firefox window.

Confirm installation of the extension by clicking the Add button.

SecureAnyBox extension for Firefox is sucessfully installed.
At the Downloads page, click the Chrome Extension for SAB link and from the Chrome web store install the web extension.
When accessing a web page with a login form, the SAB vault icon (
![]() ) appears in the password entry field. For example, at paypal.com
) appears in the password entry field. For example, at paypal.com

After clicking on the vault icon, a login window will appear, asking you to log on to the SAB server. Launcher remembers successful login until restart, logout, or session timeout if it set on the server.

Note: When you use the extension for the first time, you may first see the SAB Server Address window. Use the same address you use to access the SAB web interface.

If the KeyShield SSO login configured on the SecureAnyBox server and the user is logged to KeyShield, this part of the authentication performs automatically.
If the user has a two-factor authentication set, the second-factor code is requested after login.

After successful authentication to SecureAnyBox server, a window will appear with a menu of records that can be used to log in to the web service. Displayed are all relevant accounts, from all Safe Boxes into which the user has access.

Accounts are displayed ranked by relevance calculated based on data stored by SAB. The default search is based on URLs in the Address and Login Site fields. If the relevant account is stored in SecureAnyBox but does not have a filled URL in the appropriate fields, it is still possible to search for it manually, by entering the search term (e.g., name, description, etc.) into the Find field.
After selecting the account (by double-clicking, pressing Enter, or selecting and clicking OK), you are asked to enter the Access Code.
The access code can be temporarily cached by Launcher (see Settings), so the Access Code will not be required for repeated accesses within the time limit.

After entering a valid Access Code, the launcher fills in the selected credentials to the login fields.
If the login is divided into several steps (e.g., Google account, etc.), or if the password field is non-standard and does not display the extension icon, you can use the context menu instead of clicking the icon. The context menu is displayed by right-clicking in the user name or password field.
Under the SecureAnyBox section, the Fill username, Fill password options are available (in both cases, the record selection dialog will be displayed). If an entry has already been used on this page, additional options are available: “Enter username for...” and “Enter password for...”

Using the context menu it is possible to create a new account, directly from the website, without having to use the SecureAnyBox web interface.
In the context menu click
Add account to display a form with a pre-filled Name, Address, and Login Site.

Into the
Create in Safe Box field, select the Safe Box into which you want to create a new account by clicking the button with three dots.
Into the
Username filed, enter the username.
Into
Password and
Repeat password fields, enter the password. In addition to manual entry, the password can be generated.
When generating the password, it is possible to choose from 2 preset modes:
Very strong (password is generated from all characters) and
Strong (special and easily interchangeable characters are omitted).
If you need to meet any specific password requirements (number of characters or numbers, special characters, etc.), you can create your own generating rule by clicking the
gear button (
![]() ) next to the
Generate button.
) next to the
Generate button.

When all values set, an account can be saved by clicking the OK button. Depending on the settings of remembering of the access Code, it may be necessary to enter the access Code again.
SAB Manager plugin allows you to work with data in Safe Boxes via Total Commander.
Open zip file in Total Commander (64-bit version). Total Commander automatically detects that it is a plugin and guides you through the installation. All dialog boxes have to be confirmed (Yes / OK).




After the SecureAnyBox Manager plugin installed, the SecureAnyBox directory is available as a Network Neighborhood place. To open the directory for the first time, it is necessary to enter the SecureAnyBox server address, login information and etc. Next time, the connection will be opened, the user will be asked to enter the password only.
Select “Network Neighborhood” as a disk drive

The SecureAnyBox directory is now available as Network Neighborhood place.

Each time you access the plugin directory, is created new directory named SAB-hh.mm.ss (where hh.mm.ss is the current time).

In this directory, you have to create a connection to the SAB server using the F7 key.
As a first step enter a connection name.

In the next step, enter the SecureAnybox URL address. (Address can be obtained from any Safe Box detail from the menu Import... > Copy SAB address).

Next, enter the user name of the user who will connect to the SAB

and domain name. If you are using only one domain (the default System domain), you do not have to enter its name.

The newly created connection is displayed as a folder.

You can view the saved connection details by pressing Alt + Enter.

The connection to the server is made by entering the connection folder (a password will be requested). After entering the password, a list of safeboxes is displayed.

Enter - Copies a password to the clipboard from your account, secret account, and credit card.
The plugin allows you to edit file or certificate in the appropriate program associated with the specific file type. After saving the modified file, it creates a new version of the file.
Alt+Enter - Displays properties of account, secret account etc.

F3 View - Displays the file if the record is File or Certificate.
F4 Edit - Edits a file if the record is File or Certificate.
F5 Copy - Copies the file (s) or certificate (s) from / to SecureAnyBox. Only file and certificate records can be copied.
F6 Move - Move is not supported.
F7 New Folder - Only in connection overview. Creates a new connection and writes data (connection name, URL, domain and username) to the registry.
The plugin does not create new records.
F8 Delete - Deleting records is not supported.
At the page Deleted records, a user can manage deleted records (such as Safe Boxes, Safe Box Groups, Accounts, etc.)
Deleted records can be permanently removed or restored to the original location.

You can remove permanently multiple records at one time by selecting them and clicking on the
Remove selected
button. The button is only displayed if some of the deleted records are selected. Removing selected records have to be confirmed.
Selected deleted records can be restored by clicking the
Restore selected
button. The button is displayed if some of the deleted records are selected.
Deleted records can be also restored to the original location by clicking on the restore icon (
![]() ) at the end of a row. Restoring the record have to be confirmed.
) at the end of a row. Restoring the record have to be confirmed.
Audit log page displays a log of users actions in Safe Boxes, Safe Box Groups, White Envelopes and all records inside them. Depending on the user role, only actions of currently logged user or actions of all users are shown.

User can filter displayed actions in the log by entering a text into the search field. Searching is possible above values of the columns IP, User, and Action.
Results of filtering the audit log can export by clicking on the
Download
button.
The audit log can be refreshed manually by clicking on the
Refresh
button or automatically by clicking on the
Enable autorefresh
button. Automatic refresh of the audit log is possible to turn off by clicking on the
Disable autorefresh
button.
The Access to Records report shows all records into which the selected user has entered the access code, to view encrypted values. To run the report, select a user.
In report results, records into which currently logged user don’t have access, won’t be displayed even though the selected user accessed them. To view all records which selected user accessed, use the report with the same name in Audit part.

In report results, you can click the record name. After clicking, a record page displays in a new tab, where you can check details or even change the encrypted values. If the password has changed, the record is no longer displayed in the report results for the selected user because that user did not access the changed password.
To actualize report results, click the
Refresh
button.
The Access to Safe Box report shows all records from selected Safe Box into which users have entered the access code, to view encrypted values.
In this report, Safe Boxes into which currently logged user does not have access, cannot be selected. To see results for any Safe Box (even the private one) within a currently logged user’s domain, use the report with the same name in Audit part.

In report results, you can click the record name. After clicking, a record page displays in a new tab, where you can check details or even change the encrypted values. If the password has changed, the users who access to record are no longer displayed in report results because they did not access the changed password.
To actualize report results, click the
Refresh
button.
Watching report
displays Safe Box Groups, Safe Boxes, and records which is currently logged user watching on the selected level.

Following icons are used to distinguish whether the watching is set explicitly or is inherited from the parent level:
|
|
Watching of changes is set explicitly for that level. Accesses are not watched. |
|
|
Watching of changes is inherited from the parent level. Accesses are not watched. |
|
|
Watching of accesses to encrypted data is set explicitly for that level. Changes are not watched. |
|
|
Watching of accesses to encrypted data is inherited from the parent level. Changes are not watched. |
|
|
Watching of changes and accesses to encrypted data is set explicitly for that level. |
|
|
Watching of changes is set explicitly for that level. Watching of accesses to encrypted data is inherited from the parent level. |
|
|
Watching of changes is inherited from the parent level. Watching of accesses to encrypted data is set explicitly for that level. |
|
|
Watching of changes and accesses to encrypted data is inherited from the parent level. |
If selected Safe Box inherits watching accesses and/or changes from the Safe Group, then the Safe Box Group will be displayed in the report results for selected Safe Box also.

Report
Permissions
displays permissions of the selected user to all Safe Boxes, Safe Box Group and domain' root level. The results are filtered by permissions of the currently logged user. It means that the currently logged user will only see selected user' permissions for Safe Boxes, Safe Box Groups and domain' root level, for which currently logged user has permissions also.
To display results, click the
Select user
button and wait for a list of users. In the displayed list, select a user for which you want to display results.

The following icons are used to distinguish the level for which permissions set:
![]() - Root level of domain
- Root level of domain
![]() - Shared (non-private) Safe Box Group
- Shared (non-private) Safe Box Group
![]() - Private Safe Box Group
- Private Safe Box Group
![]() - Shared (non-private) Safe Box
- Shared (non-private) Safe Box
![]() - Private Safe Box
- Private Safe Box
To manage permissions for the specific level, click its name in search results. After clicking the name, in new browser tab will be opened the Sharing & Permissions page for that level. At the page can be managed permissions for other users.
Report
Permission Templates Assignment
shows all permission templates set for the selected user tag. The results are filtered by permissions of the currently logged user. It means that the currently logged user will only see permission templates for Safe Box Groups and Safe Boxes, for which the currently logged user has permissions.
To display results, click the
Select user tag
button and wait for a list of user tags. In the displayed list, select a user tag for which you want to see results.

The following icons are used to distinguish the level for which permissions set:
![]() - Root level of domain
- Root level of domain
![]() - Shared (non-private) Safe Box Group
- Shared (non-private) Safe Box Group
![]() - Private Safe Box Group
- Private Safe Box Group
![]() - Shared (non-private) Safe Box
- Shared (non-private) Safe Box
![]() - Private Safe Box
- Private Safe Box
Report
Passwords Audit
displays all records that a logged on user has access to, and for passwords of displayed records, counts password entropy, time to crack the password, and alerts for duplicates of passwords.
To display results, select a level of audit:
When the level of audit selected, a user is prompted to enter the access code. Have you forgotten the access code?
After entering the access code, SecureAnyBox checks all records which can decrypt with an entered access code, obtains passwords from them and counts results of the report.
To calculate passwords entropy and other values, SecureAnyBox uses password strength estimator
nbvcxz
. The password strength estimator inspires by password crackers.
Strength estimation accomplishes by running a password through different algorithms and looking for matches in any part of the password on word lists (with fuzzy matching), common dates, common years, spatial patterns, repeating characters, repeating sets of characters, and alphabetic sequences.
Each of these represents a way, how an attacker may try to crack a password. More information...
The calculation of the password entropy will be more accurate if custom password dictionaries added.
We strongly recommend adding a dictionary of the commonly used passwords in your language, a dictionary with names of towns, streets in your area etc. You should also add the default passwords used by your company to the dictionaries.
A password dictionary is usually .txt file with one word per line. Should not find a suitable password dictionary, you can create a dictionary by yourself.
There are two types of password dictionaries:
Password dictionaries need to be added to "<SecureAnyBox folder>/files/dictionaries/<type of dictionary>" folder
Examples:
You want to add a dictionary with names of cities and streets near you. All names are text file, each one on a single line.
In that case, the dictionary is unranked (does not matter if names are alphabetically ordered or not). Please add the dictionary to
unranked folder in the dictionaries folder (e.g., “C:\\SecureAnyBox\files\dictionaries\unranked\”).
You want to add a dictionary with the most common passwords, ordered by the frequency of password usage.
In that case, the dictionary is ranked. Please add the dictionary to
ranked folder in the dictionaries folder (e.g., “C:\\SecureAnyBox\files\dictionaries\ranked\”).
When dictionaries added, it is necessary to restart the SecureAnyBox. After restart, the dictionaries are applied to the calculation of the password entropy.

When loaded, in results are displayed Safe Box Groups and Safe Boxes, stored at the root level. By clicking on the plus icon (
![]() ), you can see more detailed results – for each Safe Box inside a Safe Box Group or each account and secret account in a Safe Box.
), you can see more detailed results – for each Safe Box inside a Safe Box Group or each account and secret account in a Safe Box.
Results for Safe Box Group and Safe Box displays the lowest value of Password Entropy of all records inside the Safe Box or Safe Box Group and how many passwords of records inside the Safe Box or Safe Box Group are duplicit.
In order to display the report results better organized, detailed results can be collapsed into results for Safe Box or even Safe Box Group.
Results for Safe Box Group and SafeBox displays the lowest Password Entropy of all passwords inside and how many passwords of records inside the Safe Box are duplicate.
After clicking on the record name, the record page displays in the new tab. On the records page, you can also change the password to a more secure one.
To refresh the report results, click the
Run Report
button again.
Password entropy is a measurement of how unpredictable a password is. The higher the value, the better.
Based on password entropy value, SecureAnyBox recognizes four levels of how secure the password is.
| Password security | min. | max. | Description | |
|---|---|---|---|---|
| really bad |
|
0 | 20 | password should be changed immediately |
| unsatisfactory |
|
20 | 35 | password does not meet security standards, should be changed |
| satisfactory | 35 | 50 | password meets security standards, but it can be better | |
| really good |
|
50 | password is really secure |
Depending on the password strength, SecureAnyBox counts how long it would take to crack your password online and offline. The longer a and more unpredictable your password is, the better.
SecureAnyBox checks passwords for duplicity. If there are any duplicates, a number of duplicate passwords displays. Due to security, we recommend changing duplicate passwords to unique ones.
If the number of duplicates is lower or equal to five, a warning icon (
![]() ) displays. If the number of duplicates is higher than six, an error icon (
) displays. If the number of duplicates is higher than six, an error icon (
![]() ) displays.
) displays.
Next, to the number of duplicates, you can click the button (
 ) to show records with the same password.
) to show records with the same password.
Date and time when the password changed last time.
The elapsed time since the last password change. If the time since change is higher or equal than two years, a warning icon (
![]() ) displays.
) displays.
Report
Search for password
allows the user to see which records have a particular password. To run the report, enter the password you want to search for into the search field. After the password entered, click the search button (
 ) or press Enter key. The entered password can be viewed by clicking the eye button (
) or press Enter key. The entered password can be viewed by clicking the eye button (
![]() ) anytime.
) anytime.
Once the Access code entered, SecureAnyBox decrypts all passwords to which the user has access. Then compares each decrypted password with the searched one and all records with the same password displays in the report results. SecureAnybox also computes the entropy of the password and displays it beside the search field. More about the entropy...
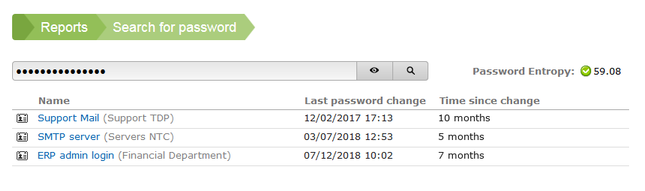
The audit is a part of SecureAnyBox application, accessible only to users with Auditor role, for auditors are three reports and the audit log of all parts available. Each auditor can audit within a domain, in which belongs. The only exception is an auditor from the System domain which can audit all domains.
The Access to Records report shows all records into which the selected user has entered the access code, to view encrypted values. To run the report, select a user.

In report results, all records into which currently logged user have access, are blue. After clicking on such record, a record page displays in a new tab, where you can check details or even change the encrypted values.
If record name is black, currently logged user hasn’t access to a record and nothing happens after clicking on it.
In a case, record name is crossed out, the record is deleted but can still be restored on the Deleted page.
If the password has changed, the record is no longer displayed in the report results for the selected user because that user did not access the changed password.
To actualize report results, click the
Refresh
button.
The Access to Safe Box report shows all records from selected Safe Box into which users have entered the access code, to view encrypted values.

In report results, all records into which currently logged user have access, are blue. After clicking on such record, a record page displays in a new tab, where you can check details or even change the encrypted values.
If record name is black, currently logged user hasn’t access to a record and nothing happens after clicking on it.
In a case, record name is crossed out, the record is deleted but can still be restored on the Deleted page.
If the password has changed, the record is no longer displayed in the report results for the selected user because that user did not access the changed password.
To actualize report results, click the
Refresh
button.
Report
Permissions
displays permissions of the selected user to all Safe Boxes, Safe Box Group and domain' root level. Unlike from report in Reports part, results of this report don’t filter by permissions of the currently logged user. That means that the currently logged user will see all selected user' permissions for Safe Boxes, Safe Box Groups and domain’s root level, even for which currently logged user has no permissions.
To display results, click the
Select user
button and wait for a list of users. In the displayed list, select a user for which you want to display results.

The following icons are used to distinguish the level for which permissions set:
![]() - Root level of domain
- Root level of domain
![]() - Shared (non-private) Safe Box Group
- Shared (non-private) Safe Box Group
![]() - Private Safe Box Group
- Private Safe Box Group
![]() - Shared (non-private) Safe Box
- Shared (non-private) Safe Box
![]() - Private Safe Box
- Private Safe Box
To manage permissions for the specific level, click its name in search results. After clicking the name, in new browser tab will be opened the Sharing & Permissions page for that level. At the page can be managed permissions for other users.
Report
Permission Templates Assignment
shows all permission templates set for the selected user tag. Unlike from report in Reports part, results of this report don’t filter by permissions of the currently logged user. That means that the currently logged user will see all selected user' permissions for Safe Boxes, Safe Box Groups and domain’s root level, even for which currently logged user has no permissions.
To display results, click the
Select user tag
button and wait for a list of user tags. In the displayed list, select a user tag for which you want to see results.

The following icons are used to distinguish the level for which permissions set:
![]() - Root level of domain
- Root level of domain
![]() - Shared (non-private) Safe Box Group
- Shared (non-private) Safe Box Group
![]() - Private Safe Box Group
- Private Safe Box Group
![]() - Shared (non-private) Safe Box
- Shared (non-private) Safe Box
![]() - Private Safe Box
- Private Safe Box
The Audit log page displays a log of users actions in Safe Boxes and SecureAnyBox part of the application. The audit log results are filtered by domain into which currently logged user belongs. The only exception is an auditor from System domain which can see audit log of user actions from all domains.

It is possible to filter displayed actions in Audit log by clicking buttons
SecureAnyBox logs
or
Safe Boxes logs
. The filter can be turned off by clicking the
All logs
button.
You can also filter displayed actions in the log, by entering a text into the search field.
Searching runs above values of the columns IP, User, and Action.
Results of filtering the audit log can be exported by clicking on the
Download
button.
The audit log can be refreshed manually by clicking on the
Refresh
button or automatically by clicking on the
Enable autorefresh
button. Automatic refresh of the audit log is possible to turn off by clicking on the
Disable autorefresh
button.
If enabled in the Configuration, auditor can archive the audit log by clicking the Archive log records button. After clicking the button, it is necessary to confirm archiving.

The Stations page intended for management of registered stations. After loading the page, users can see a table of registered stations for selected Agent Configuration.
To change the Agent Configuration, click on the
Select Config
button and in a displayed list select the configuration. After a different configuration is selected, the list of the registered domain is actualized and displays stations registered in the currently selected configuration.
Registered stations are possible to sort by any displayed column. To sort the stations, click on the column header. It is also possible to add more columns to the table of stations (IP address, Timezone, Default User, Station Registration). To configure a displaying of additional columns, go to the Agent Configuration page.
Registered stations can be filtered by the date of registration and last access. User with role Administrator from System domain can also see (and delete) inaccessible stations. Stations are inaccessible if the Agent Configuration with which the stations are registered is deleted.
As the IP address of the station displayed the address which station had during the last registration. IP addresses are not unique.
Stations have to be registered to get passwords for them. Once the station is registered, it is possible to get the password by clicking on a row in a table of stations. After clicking on a row with the registered station, the
Get Password
page will load with prefilled values according to the values specified in the registered station.
Stations may be registered by SecureAnyBox agent or manually. After successful installation of SecureAnyBox Agent and applying the configuration, the SecureAnyBox Agent checks if the applied configuration matches the Agent configuration on the server. If so, the station would be registered automatically (it might take 10 minutes). In some cases, the station on which the SecureAnyBox Agent installed, does not have access to the server and cannot be registered automatically. But the station can be registered manually.
To register the station manually, click on the
Register station
button and wait for displaying the station’s form.
If the station name is changed. It is necessary to re-configure SecureAnyBox Agent, which will later register the station with a changed name. Original station registration can be deleted manually from the SecureAnyBox later.

In this field select the agent configuration, which is the same as the configuration of a SecureAnyBox Agent installed on a registered computer.
Selection of incorrect configuration leads to generating passwords that do not work.
Selected agent configuration is pre-filled into this field and can be changed by clicking on the folder icon (
![]() ) and selecting another one from a list of agent configurations.
) and selecting another one from a list of agent configurations.
Select the platform (operating system) of a registered station.
The platform is important for identifying a username of an administrator, for whom a password will be generated. Settings of the agent configuration limit selection of platforms.
Station name has to be in a format selected in the agent configuration.
NETBIOS = use NETBIOS station name.
Fully Qualified DN = use full Active Directory station name with the domain (e.g., STATION1.domain.local).
SID = use station unique SID (e.g., S-1-5-21-3623811015-3361044348-30300820-1013).
Select a time zone which is set on the registered station. The timezone is used for the definition of station’s actual time compared to the actual time and the timezone of the server.
For example, if the server has set timezone as “(GMT) Dublin, Edinburgh, Lisbon, London” , and the station has set timezone as “(GMT -08:00) Pacific Time (US & Canada)”. The password for this station will be generated for date and time which is about 8 hours lower than the actual time of the server.
To delete registered station, please click on the cross icon (
![]() ) at the end of a row. Deleting the station have to be confirmed.
) at the end of a row. Deleting the station have to be confirmed.
It is also possible to delete multiple stations at the same time. To select a station to delete, check the checkbox in the first column. After the selection is complete, click the Delete selected button.

At the Get Password page is possible to obtain a password for a station. To get a password for the station is necessary to install SecureAnyBox Agent on the station. More about SecureAnyBox Agents...

To obtain the station’s password, please follow these steps:
In a case that you are obtaining a password for the registered station, all values pre-fill automatically.
Select the agent configuration which is the same as the configuration of SecureAnyBox Agent installed on the station.
Select an operating system of the station. Settings of the agent configuration limit selection of operating systems.
Please check and eventually correct the local date. The time automatically sets according to server time.
Enter the station’s name. The name has to be in a format specified in the agent configuration.
NETBIOS = use NETBIOS station name.
Fully Qualified DN = use full Active Directory station name with the domain (e.g.,STATION1.domain.local).
SID = use station unique SID (e.g.,S-1-5-21-3623811015-3361044348-30300820-1013).
To obtain a password, the station has to be registered. If a station with entered name is not registered, the user will be prompted to register the station before obtaining a password.
Check the User for whom the password will work. The user is pre-filled according to settings in the agent configuration.
Check and eventually correct a timezone set on the station. Depending on the previously set Local Date and Time and selected timezone, the Station Date and Time set.
Click on the Show password button.
After clicking on the Show password button, the Station password page loaded.

After 60 seconds you will be redirected back to the Get Password page.
At the Downloads page, it is possible to download SecureAnyBox Agent, its configuration, and SAB Launcher.

SecureAnyBox (SAB) Launcher is an MS Windows (.NET Framework 4.5.2 or higher required) application delivered as a msi package. After installation, the application runs in the system tray and registers the custom URI scheme for sab:// links from the SecureAnyBox web interface.
After SecureAnyBox Agent registers the station, its IP address is also registered. By clicking on the station IP address at the Stations page, SecureAnyBox Launcher launches Remote Desktop application and connects to the registered station.
SecureAnyBox Launcher is also used in Safe Boxes. More information...
SecureAnyBox Agent is a system service/daemon that ensures login to the station using the password obtained in SecureAnyBox. The password can be obtained at the Get Password page or from the Ticket. Configured SecureAnyBox Agent works completely autonomously even without connection to the server. If a connection to the server is available, the SecureAnyBox agent automatically performs station registration.
To suuccessfully install SecureAnyBox Agent is necessary to download the Agent Configuration file also. Please download the appropriate configuration file by clicking the configuration name. If the required configuration does not display in the list of downloads for your platform, please verify that the Agent Configuration includes settings for that platform as well.
Installation steps of SecureAnyBox Agent:
After the SecureAnyBox Agent successfully installed and the configuration is applied, SecureAnyBox Agent verifies whether the configuration used matches the agent configuration on the server. If so, the station will be automatically registered (this may take 10 minutes). In some cases, the station on which the SecureAnyBox Agent installed does not have access to the server and cannot be registered automatically. Such a station can be registered manually.
Troubleshooting:
In a case of problems with SecureAnyBox Agent, please refer to the log. Logging of the SecureAnyBox Agent on the Linux and macOS platform runs automatically into a file var/log/secureanybox-agent.log. On Linux, you can even enable detailed debug logging in /etc/secureanybox/settings by renaming (or copying) the “settings.example” file to “settings” and uncommenting the “export SECUREANYBOX_AGENT_DEBUG = true” line.
The log file on the macOS platform is possible to view in the Console. The log file on the MS Windows platform is possible to view by using SAB Monitor utility (download in SecureAnyBox/Downloads) or in the Windows Event Viewer.
If the station is not registered even though the station has access to the server, the most likely reason is an incorrect configuration of the agent (e.g. the configuration has been changed on the server but not on the station) or a problem with https certificate verification. The https certificate must be imported as trusted on the agent station. On Linux, it must be located in a Keystore that uses Python for certificate verification. This can be checked in the terminal using the command:
python -c 'import urllib2; import sys; resp = urllib2.urlopen("https://your.secureanyboxserveraddress.com"); rcode = resp.getcode(); body = resp.read(); print rcode; print ""; print body;'
If certificate validation is successful, on the first row of the response is code 200.
When the certificate validation fails, an error is displayed:
urllib2.URLError: <urlopen error [SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed (_ssl.c:590)>
If urllib2 not found
python ––version
or
python -v
Urllib2 is a built-in package of Python 2.x.x. To be able to run urllib2, it is necessary to have Python 2.x.x (recommended 2.7.18) installed properly. Some distributions of Linux may not have full version of Python 2.7.x installed. Try re-installing it.
wget https://www.python.org/ftp/python/2.7.18/Python-2.7.18.tgz
sudo tar xzf Python-2.7.18.tgz
cd Python-2.7.18/
sudo ./configure
sudo make altinstall
Tickets are intended for sharing access to getting passwords for the stations. Once the ticket created, it can be shared with anybody (even with people without access to SecureAnyBox). Sharing a ticket is a convenient method for giving access to
registered station passwords only for a limited time. For example, tickets can be shared with external technicians.
Shared access to passwords can be limited according to the specification of a ticket.
When the Agent Configuration is selected only, then based on the ticket is possible to get passwords for all
registered stations with the same Agent Configuration as is selected.
If the Agent OS is also selected, then through the ticket is possible to get passwords for all
registered stations with same Agent Configuration and operation system as is selected.
When the station name is specified too, then on the basis of the ticket is possible to get a password for the one station only.
The validity of the ticket is limited. The person, to whom the ticket was shared, can get a password between dates and times specified in fields
Valid from and
Valid until only.
It is possible to restrict the usage of tickets, by setting subnets. When the ticket has subnet set, it is possible to obtain a password from the ticket only if the device’s subnet is the same as is set in the ticket. In the ticket, it is possible to set multiple subnets.
To create a ticket, please click the New Ticket button. After clicking, a form for creating the ticket displays. After all values entered, please click on the OK button to confirm the ticket.

While saving the ticket, a unique identifier of the ticket generated. This identifier is displayed in a message after the ticket created.

Select the Agent Configuration. Agent configuration must be the same as the configuration SecureAnyBox Agent installed on the station for which the ticket will create.
In case that a ticket will be saved with the selected Agent Configuration only, it will be possible to get the password for all the stations where the SecureAnyBox Agent with the same configuration installed.
The description should characterize the purpose of the ticket.
For example, if the ticket will be used by external workers, in the description can be specified for whom and why the ticket created.
In the case that the ticket will save without any description, and the description will be generated. The result of generating the description will be “Ticket {number of the ticket}” (e.g. Ticket 1, Ticket 2 and so on).
Select the operating system. Settings of the Agent Configuration limit selection of the operating systems.
Selecting the operating system is optional.
When the operating system is selected, through the ticket is possible to get passwords only for stations with the same OS.
If the operating system is not selected, then the last selected platform will be used while generating a password for the station.
Name of the
registered station, for which the ticket will be created. Station name must be in the same format as is specified in the Agent Configuration.
NETBIOS = use NETBIOS station name.
Fully Qualified DN = use full Active Directory station name with the domain (e.g.,STATION1.domain.local).
SID = use station unique SID (e.g.,S-1-5-21-3623811015-3361044348-30300820-1013).
If the station name not specified in a saved ticket, it will be possible to specify the name while getting a password for the stations. Through such a ticket will be possible to get the password for each
registered station with the same Agent Configuration and operating system as are selected in the ticket.
The user for whom will be generated the password. The user field has prefilled value base on values specified for the selected operating system in the Agent Configuration.
Date and time from which the ticket is valid, and based on the ticket, it is possible to get a password.
Date and time until which the ticket is valid, and based on the ticket, it is possible to get a password.
Ticket is only valid when accessed from specified subnets or addresses. If no subnet or address is listed, ticket access not restricted by client address.
Subnets can be entered in three formats – standalone IP address, IP address/subnet mask where subnet mask can be specified in IPv4 format or in CIDR notation format - e.g.: 172.22.38.19 or 172.22.38.1/255.255.255.0 or 172.22.38.1/24
The IP address must be in IPv4 format. IPv6 not supported.
Ticket is only valid when accessed from specified subnets or addresses. If no subnet or address is listed, ticket access is not restricted by client address.
Subnets are possible to enter in three formats – standalone IP address, IP address/subnet mask where subnet mask can be specified in IPv4 format or CIDR notation format - e.g.: 172.22.38.19 or 172.22.38.1/255.255.255.0 or 172.22.38.1/24
IP address must be in IPv4 format. IPv6 not supported.
If the ticket is not enabled, it can not be used.
To edit an existing ticket, please click the ticket’s row in a table. After clicking, an edit form displays.

In the edit form, it can be changed all values except the agent configuration. After all changes are made, please confirm them by clicking on the OK button.



The Audit log page displays a protocol of getting passwords for stations and using tickets. Depending on the user role are shown only actions of currently logged user or actions of all users.

You can filter displayed actions, by entering a text into the search field. Searching is possible above values of the columns IP, User, and Action.
Results of filtering the audit log can be exported by clicking on the
Download
button.
The audit log can be refreshed manually by clicking on the
Refresh
button or automatically by clicking on the
Enable autorefresh
button. Automatic refresh of the audit log is possible to turn off by clicking on the
Disable autorefresh
button.
At the Agent Configuration page, you can set some General setting for SecureAnyBox like columns at the Station page or Registration interface, or you can set Agent Configuration and the LDAP Agent. You can also change the configuration password and download the SecureAnyBox configuration file.

You can configure which columns display at the Stations page and alternative interface which is only intended for registration of stations. If alternative interface enabled and set, registration interface hostname and HTTPS port exported into the SecureAnyBox Agent configuration.
We recommend to enable and set registration interface because the registration of SecureAnyBox Agents will not be affected by any changes (e.g., of hostname, address, port) in the configuration of SecureAnyBox server.

Optional registered stations table columns definition
Show IP Address column
Show Time Zone column
Show Default User column
Show Station Registration date column
SecureAnyBox server station registration web interface/API configuration.
Enable standalone HTTPS interface used only for station registration
SecureAnyBox station registration (HTTPS) interface IP address.
SecureAnyBox station registration (HTTPS) interface port.
PKCS #12 file with a private key and corresponding certificates used for HTTPS web interface. You can create a self-signed certificate file by clicking the Create self-signed SSL certificate button in the left bottom corner of this form.
HTTPS key store password. It is used to read HTTPS keys and certificates. In a case you create the HTTPS keystore file by clicking the Create self-signed SSL certificate button, the keystore password entered automatically.
List of hostnames for SecureAnyBox station registration interface (HTTP).
If the HTTPS keystore certificate is imported as trusted on your Linux station, it is possible to verify in the terminal using the command:
python -c 'import urllib2; import sys; resp = urllib2.urlopen("https://your.secureanyboxserveraddress.com"); rcode = resp.getcode(); body = resp.read(); print rcode; print ""; print body;'
If certificate validation is successful, on the first row of the response is code 200.
When the certificate validation fails, an error is displayed:
urllib2.URLError: <urlopen error [SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed (_ssl.c:590)>
If urllib2 not found
python ––version
Urllib2 is a built-in package of Python 2.x.x. To be able to run urllib2, it is necessary to have Python 2.x.x (recommended 2.7.18) installed properly. Some distributions of Linux may not have full version of Python 2.7.x installed. Try re-installing it.
wget https://www.python.org/ftp/python/2.7.18/Python-2.7.18.tgz
sudo tar xzf Python-2.7.18.tgz
cd Python-2.7.18/
sudo ./configure
sudo make altinstall
To generate passwords for stations, each station must have SecureAnyBox Agent installed with a proper configuration. In the Agent configuration, you can configure for which platforms can be used, a password pattern, a password seed base, for which user or user group the password will be generated.
After each modification of Agent Configuration, the SecureAnyBox Agent (respectively Agent Configuration) installed on stations must be updated or generated passwords might not work.

To add a new configuration, please click on the add Configuration button and wait for Agent Configuration form to display. After all values are set, please click on the OK button. To use a new Agent configuration, the SecureAnyBox have to be restarted first.

Please enter SecureAnyBox Agent Configuration Name. Configuration name must start with a letter and contain only letters, numbers and underscore.
Password pattern which will be used to generate passwords for stations.
Each letter in the pattern corresponds to letter in the generated password.
See examples of the password pattern
Characters allowed in the password pattern and their meaning:
v – lowercase vowel a,e,i,o,u,y
V – mixed case vowel (A,E,I,O,U,Y,a,e,i,o,u,y)
Z – upper case vowel
c – lowercase consonant (b,c,d,f,g,h,j,k,l,m,n,p,q,r,s,t,v,w,x,z)
C – mixed case consonant
z – upper case consonant
l - any alphabet character (vowel or consonant) - lowercase
A - any alphabet character - mixed case
u – upper case alphabet
d - digit (0-9)
s – special character (.,@,&,*,(,),<,>,_,],[,%,$,#,\,/,?,;,-,:)
n – digit or special character
\ - escape character - next character is used as is (e.g., pattern ‘\-‘ outputs ‘-‘ in the resulting password)
* - any allowed character
1 – character according to Pattern Characters 1 setting
2 – character according to Pattern Characters 2 setting
3 – character according to Pattern Characters 3 setting
Default pattern is CVCVdddCVCCVdC (this might generate passwords such as: wEHe063heFme4p).
For example, you can set a password pattern as ‘\p\a\s\sddddddd‘ and this might generate passwords such as ‘pass1762885‘ or ‘pass5687412‘.
By setting the Pattern Characters, you can specify a set of characters that will be used or omitted while generating a password.
To specify a set of characters that will be
used while generating a password, please enter them into the field without any separator. (e.g.,‘abc‘). In that case, the generated password will use only specified characters.
The set of characters that will be
omitted while generating a password must begin with
^ character (e.g.,‘^0123‘). In that case, the generated password will use allowed characters except for specified ones.
For each character which should generate according to the setting of this set of characters, enter ‘1‘ into the Password Pattern.
By setting the Pattern Characters, you can specify a set of characters that will be used or omitted while generating a password.
To specify a set of characters that will be
used while generating a password, please enter them into the field without any separator. (e.g., ‘abc‘). In that case, the generated password will use only specified characters.
The set of characters that will be
omitted while generating a password must begin with
^ character (e.g., ‘^0123‘). In that case, the generated password will use allowed characters except for specified ones.
For each character which should generate according to the setting of this set of characters, enter ‘2‘ into the Password Pattern.
By setting the Pattern Characters, you can specify a set of characters that will be used or omitted while generating a password.
To specify a set of characters that will be
used while generating a password, please enter them into the field without any separator. (e.g., ‘abc‘). In that case, the generated password will use only specified characters.
The set of characters that will be
omitted while generating a password must begin with
^ character (e.g., ‘^0123‘). In that case, the generated password will use allowed characters except for specified ones.
For each character which should generate according to the setting of this set of characters, enter ‘2‘ into the Password Pattern.
This is a secret string used as a base to generate a station password. Seed Base should be unique for your configuration and is shared between the server and SecureAnyBox Agent instances. You have to distribute Seed Base together with password pattern to all SecureAnyBox Agent managed stations.
Enable MS Windows platform
Enable Linux platform
Enable macOS platform
Enable LDAP platform
Configuration encryption password. If SecureAnyBox configuration is encrypted, then is required to enter the configuration password, to create or edit Agent Configuration successfully.
SecureAnyBox Agent Configuration for Windows Platform
SecureAnyBox Agent Configuration for Linux Platform
SecureAnyBox Agent Configuration for macOS Platform
SecureAnyBox Agent Configuration for LDAP Platform
It is possible to extend or limit the visibility of the Agent Configuration by setting permitted users. If permitted users not set, the Agent Configuration is visible to all users from the domain, for which the agent configuration set as visible. To set permitted users, please add a domain or user. If domain added, the Agent Configuration is visible to all users from that domain. If a user added, the Agent Configuration is visible for that user only.
If you add a domain, the Agent Configuration will be visible for users from that domain.
If you add a user, the Agent Configuration will be visible for that user.
To edit the Agent Configuration, please click on configuration name in a list of Agent Configurations. After clicking on configuration name, details of the configuration displays.

To open Agent Configuration edit form, please click on the
Edit
button. In the Agent Configuration, you can modify all values except the configuration name.
After changes finished, please confirm them by clicking on the
OK
button. To apply changed Agent Configuration is necessary to apply changes in the SecureAnyBox configuration first.
In a case, you want to create similar Agent Configuration, as is already stored, you can copy the stored one. To copy the Agent Configuration, please click on configuration name in a list of Agent Configurations. When details of the Agent Configuration displays, please click on the
Copy
button.
After clicking on the button, please enter the configuration name, modify values, which needed to be changed and confirm new Agent Configuration by clicking on the
OK
button.
Due to security reasons, we strongly recommend changing the Password Seed Base.
To use the new Agent Configuration is necessary to apply changes in the Configuration.
To remove the Agent Configuration, please click on configuration name in a list of Agent Configurations. After clicking on configuration name, details of the configuration displays and click the
Remove
button.
Removing the Agent Configuration have to be confirmed by applying changes in the SecureAnyBox configuration.
LDAP Agent holds LDAP server connection settings used for user password changes. Without LDAP Agent it is not possible to get passwords for LDAP users.

To add new configuration of LDAP agent, please click on the add LDAP Agent button and wait for LDAP Agent form to display. After all values set, please click on the OK button. To use a new LDAP Agent configuration is necessary to restart the SecureAnyBox server first.

Unique agent identifier. Agent ID is used when generating a password for the user from LDAP.
Enable/disable this LDAP Agent
LDAP server type.
LDAP server address or addresses of multiple LDAP servers with same directory replica/mirror (for failover).
LDAP User DN used by SecureAnyBox to access LDAP directory, lookup users, change passwords, etc.
Minimum access rights:
entry/object rights – browse
cn – read, compare
objectClass – read, compare
Use ‘Create SecureAnyBox objects’ button to create the manager user automatically when using NetIQ eDirectory. If you are connecting to a directory service from another vendor, please create a manager user using your directory service management console. LDAP interface on some directory services (e.g., Active Directory) doesn’t provide access rights/permissions modification.
e.g.,cn=secureanyboxmgr,o=org or cn=secureanyboxmgr,cn=Users,dc=DOMAIN,dc=local
Please enter SecureAnyBox mgr user password.
LDAP container used as a search base for LDAP synchronization search query. When the search base not set,the search starts at the root of the LDAP tree.
e.g.,o=org or leave empty to search from the root of the tree
Uncheck to search only the immediate subordinates of the specified search base.
An alias is an entry which points to another object in the namespace – by containing its dn. Searching the entry that an alias entry points to is known as dereferencing an alias.
There are four modes of dereferencing aliases:
When set to greater than zero, SecureAnyBox will use Simple Paged Result extended control to retrieve LDAP search results in pages of a given number of entries. Some LDAP servers have a default server-side limit for the number of entries returned in the single response. For example, Active Directory servers have a default limit of 1000 objects for a single search request. Setting Search Page Size to 1000 or lower will allow SecureAnyBox to retrieve more results (than the server limit) using multiple requests. When set to 0 no paging is used and an only single request is used to retrieve all results.
When using embedded LDAP from KeyShield SSO, this value must be set to 0.
Please select the Agent Configuration for this LDAP Agent. Selected Agent Configuration has to contain settings for LDAP platform.
The domain of default user is necessary for identifying the default user while generating a password. Default user domain must be the same as set in the workstation registry otherwise login of default user via SecureAnyBox Agent won’t work.
e.g., Default user on a station is set to “COMPANY/user1” - the default user domain is “COMPANY”.
This field is available only if Active Directory set as LDAP directory service.
LDAP attribute used by LDAP authentication for user lookup. This field is available only if Active Directory set as LDAP directory service.
To edit the LDAP Agent, please click the agent name in a list of LDAP Agents. After clicking on agent name, details of the agent displays.

To open LDAP Agent edit form, please click on the
Edit
button. In the LDAP Agent, you can modify all values except the configuration name.
After changes made, please confirm them by clicking on the
OK
button. To apply changed LDAP Agent is necessary to apply changes in the SecureAnyBox configuration first.
In a case, you want to create similar LDAP Agent, as is already stored, you can copy the stored one. To copy the LDAP Agent, please click the agent name in a list of LDAP Agent. When details of the LDAP Agent displays, please click on the
Copy
button.
After clicking on the button, please enter the Agent ID, modify values, which needed to be changed and confirm new LDAP Agent by clicking on the
OK
button.
To use a new LDAP Agent is necessary to apply changes in the Configuration.
To remove the LDAP Agent, please click the agent name in a list of LDAP Agents. After clicking on agent name, details of the LDAP Agent display and click on the
Remove
button.
Removing the LDAP Agent have to be confirmed by applying changes in the SecureAnyBox configuration.
By executing LDAP Agent, you change the password(s). Which passwords are changed depends on settings of Agent Configuration.
The Agent Configuration can be set to change a password of:
If any of users to whom should be changed password is set as SecureAnyBox mgr for any LDAP connector or LDAP Agent, then the password of that user will not be changed.
To execute the LDAP Agent, please click the agent name in a list of Agent Configurations. After clicking on agent name, details of the LDAP Agent display and click on the Execute button.
A configuration of the SecureAnyBox application is divided into several sections. Each section can be independently edited. To change settings in the section, click on the edit button at the top of a section.

After clicking on the edit button a section’s form displays. At the bottom of each form are displayed three buttons – Test, OK, Cancel.

When changes made, you can test the new values (by clicking on the
Test
button), if they’re in a correct format and so on. If the test of values was successful, you can confirm the changes by clicking on the
OK
button.
Changed sections of the configuration will display marked with a blue checkmark.

To apply changes in the configuration, you need to restart the application by clicking on the Apply button. If changes should not be applied, click on the Revert button.

After clicking the Configuration button in the menu, a Summary page of Configuration displays. At this page, configured LDAP connectors and server messages are displayed.
For each of LDAP connectors, a status is displayed – whether communication with connector is working. After clicking on the connector’s name, settings of the connector displays.

At the Summary page, it is also possible to download the configuration.
General SecureAnyBox server configuration and Web interface/API configuration.

SecureAnyBox web (HTTP) interface address. At this address is SecureAnyBox web interface accessible from the local network.
SecureAnyBox web interface HTTP port.
Web interface HTTP (plaintext) mode. Possible values: enabled (default), disabled, API (only JSON/XML API is accessible). When HTTP mode is disabled, it is possible to set redirecting to HTTPS mode.
SecureAnyBox web interface HTTPS port.
PKCS #12 file with the private key and corresponding certificates used for HTTPS web interface. You can create a self-signed certificate file by clicking on the Create self-signed SSL certificate button in the left bottom corner of this form.

The certificate alias is used as an alias inside a keystore and as a filename for stored encrypted PKCS12 file.
The common name of the certificate represents the hostname protected by the SSL certificate. The certificate is valid only if the hostname is the same as the common certificate name.
Use the domain name of your server as the common name of the certificate. If the server is available on the Internet using the “https://secureanybox.domain.com:8996” URL, use “secureanybox.domain.com” as a common name.
Enter the certificate validity in years (1-10).
The RSA key size indicates the length of the encryption key of the corresponding encryption algorithm. The RSA key size is given in bits. The minimum recommended RSA key size is 2048 bits.
Organization unit name used in certificate subject – leave empty if not needed.
Organization name used in certificate subject – leave empty if not needed.
Country code used in certificate subject – leave empty if not needed.
Alternative Subject Names – additional domain names or IP addresses used to access SecureAnyBox SSL interface
HTTPS key store password. It is used to read HTTPS keys and certificates.
SecureAnyBox web (HTTP) interface hostnames. Setting multiple hostnames is possible. All hostnames specified in the hosts files on stations must be specified here. Otherwise, the user with an unknown hostname, cannot access SecureAnyBox.
Base application URL. For example, if you set the app path to ‘/sab’, SecureAnyBox will be accessible at http://server:port/sab/. New app path will apply after restarting the SecureAnyBox.
App URL. At this address is SecureAnyBox web interface accessible for users.
When SecureAnyBox is behind a reverse proxy server, it is necessary to enter the trusted proxy IP address (or multiple addresses) to enable KeyShield SSO integration.
The server will not send Content-Security-Policy header for login.page. This can be used for example to allow third-party SSO solutions (like NetIQ NAS) to use custom login.page or insert inline scripts.
PKCS # 12 file that contains the private key and corresponding certificate for the HTTPS reverse proxy server interface. This file must be uploaded if users access the SecureAnyBox server through the HTTPS interface of a reverse proxy server and want to use the public HTTPS key API.
Reverse proxy server HTTPS key store password. Used to read the public key of the reverse proxy server. The public key is available through the HTTPS public key API.
Please select the default language of the SecureAnyBox web interface. This language will be automatically pre-set to all users. Each user can change the language in the User Preferences.
Diagnostic log configuration. You can set the log level for specific parts of SecureAnyBox or a count of lines loaded into the browser into the current log view.

Default log level. If the log level for a specific part not set, the default log level used.
Core engine log level
Internal SecureAnyBox services and database log level
API calls log level
Authentication and authorization log level
KeyShield SSO authentication and WebSockets log level
Limits number of lines loaded into the browser in current log view.
Configure settings of the connection between SecureAnyBox and Syslog server. You can also set syslog facility, event source and log level of records sent to the syslog server. You can establish multiple syslog connections — for each syslog server, one for audit log and second for diagnostic log and so on.

Please enter unique ID of connection with a Syslog server
Enable/disable this connection.
Syslog server address. The server address can be entered as an IP address (e.g., “172.22.13.1”) or as a domain name (e.g., “syslog.tdp.cz”)
Syslog server port.
Desired facility value for log messages sent to syslog. A facility code is used to specify the type of program that is logging the message. Messages with different facilities may be handled differently.
Please, select an audit record format (CSV or CEF) sent to the syslog target.
Records in
CSV (Comma-separated values) contains the same information as records in the Audit log of application.
Records in
CEF (Common Event Format) contains the most relevant event information, making it easy for event consumers to parse and use them. CEF format of records can be more detailed.
Examples of audit log in both formats are in the documentation.
Aug 7 10:27:43 172.22.78.100 [SecureAnyBox-audit] “SWB”,“172.22.100.105”,“System\\admin”,“GET PASSWORD”,TDPPRG,kiosek,DomAgent
Aug 7 10:27:58 172.22.78.100 [SecureAnyBox-audit] “SAFE”,“172.22.100.105”,“System\\admin”,“GET PASSWORD”,Firm,"Cisco ASR 1006 Router"
Aug 7 10:28:12 172.22.78.100 [SecureAnyBox-audit] “SAFE”,“172.22.100.105”,“System\\admin”,“VIEW ACCOUNT”,Firm,"Bank Certificate"
Aug 7 10:29:34 172.22.78.100 [SecureAnyBox-audit] CEF:0|TDP|SecureAnyBox|4.3.0|SWB.GET_PASSWORD|get password|3|src=172.22.100.105 suser=System\\admin act=GET_PASSWORD station=TDPPRG user=kiosek config=DomAgent
Aug 7 10:29:47 172.22.78.100 [SecureAnyBox-audit] CEF:0|TDP|SecureAnyBox|4.3.0|SAFE.GET_PASSWORD|get password|3|src=172.22.100.105 suser=System\\admin act=GET_PASSWORD safe=Firm rec=Cisco ASR 1006 Router
Aug 7 10:29:58 172.22.78.100 [SecureAnyBox-audit] CEF:0|TDP|SecureAnyBox|4.3.0|SAFE.VIEW_ACCOUNT|view account|3|src=172.22.100.105 suser=System\\admin act=VIEW_ACCOUNT safe=Firm rec=Bank Certificate
Send messages with this or higher log level to syslog. It is possible to set the different log level for messages sent to the syslog and for messages sent to the log of application. For records sent to the syslog server, it is not possible to set multiple logging levels for each part of the application, as in the SecureAnyBox diagnostic log. The selected logging level applies to all parts of the application.
To configure the log level of messages sent to the log of application, go to Logging part of SecureAnyBox configuration.
| Log level | Value | Log level of sent messages |
|---|---|---|
| TRACE | 0 | TRACE,DEBUG,INFO,WARN,ERROR |
| DEBUG | 1 | DEBUG,INFO,WARN,ERROR |
| INFO | 2 | INFO,WARN,ERROR |
| WARN | 3 | WARN,ERROR |
| ERROR | 4 | ERROR |
Archiving of audit log can be done manually or automatically. Manual archiving can be started at the Audit log page in the Audit part of the SecureAnyBox.
Archived audit log records will be stored in separate files on the server. Once records are archived, they cannot be viewed in SecureAnyBox.

If enabled, an auditor can run the archiving from the audit log page (in the Audit part). During the archiving, older records (than a number of months set below) will be saved in separate files and removed from the database. You will no longer be able to view them from SecureAnyBox.
Records older than the specified number of months will be archived (within the range of 1 to 240)
Enable automatic archiving of audit log records. The auditor can still start archiving audit log records on the audit log page.
Frequency of automatic archiving (daily, weekly, monthly, quarterly, semiannually, yearly)
The day of the week when archiving will start. At weekly frequency, it will be every week. At a shorter frequency, it will be the selected day in the first week of the period.
Server time in whole hours (within the range of 0 and 23), when archiving of audit records will run.
At this tab of the Configuration, it is possible to configure users and security oriented parametres of the SecureAnyBox. Such as a maximum number of login attempts, duration of the login ban and login password policy, etc.

User Authentication and Security configuration
Disclaimer message shown on login page.
User is banned (cannot log into application) after this number of unsuccessful attempts. Set to 0 to turn this feature off.
User is banned (cannot log into application) for this amount of minutes.
Inactivity timeout for user session. After this timeout expires with no user activity, the user will be logged-out.
Use of second factor (authenticator application) is either optional – enabled by user in the top right menu, or mandatory.
Enabling the login password policy allows you to set minimum password requirements – minimum length, minimum entropy, minimum number of uppercase or lowercase letters, and so on.
Login password policy determines minimum requirements for the login password.
This fields are displayed only if the Enable Login Password Policy field is checked.
Minimum length of the login password.
Minimum number of uppercase letters in login password.
Minimum number of lowercase letters in login password.
Minimum number of digits in login password.
Minimum number of special characters in login Password.
Permissions to manage users and domains
If not allowed, user manager from other than the System domain can only manage its own domain. If allowed, It can manage all visible domains.
After manually create a user who does not have a password, send this user an invitation e-mail with a link to set the password.

Settings of preferences for selecting the full name of users. The full name displays in the top right corner of the web interface and is also used in e-mail invitations, e-mail notifications and messages.
If the full name could not be selected according to settings in the first preference, the second preference settings would be tried. In a case, selecting of the full name according to both preferences is unsuccessfull, username will be displayed as the full name.
Most preferred settings how the full name of users will be selected.
Settings to apply if the first preference result is empty.
the username will be displayed as the user’s full name
Settings of preferences for selecting the short full name of users. The short full name displays in lists with users – e.g. in the users management, when adding permissions for Safe Boxes to other users, in the names of private Safe Boxes shared from another user, in reports, etc.
If the short name could not be selected according to settings in the first preference, the second preference settings would be tried. In a case, selecting of the short name according to both preferences is unsuccessfull, username will be displayed as the short name.
Most preferred settings how the short name of users will be selected.
Settings to apply if the first preference result is empty.
the username will be displayed as the user’s short name.
Backup of SecureAnyBox server is done at every midnight (if the server runs) or at the earliest possible opportunity. It is possible to set a configuration of backup and check if the backup ran.

To edit the configuration of Backup, click on the edit button and wait for a form to display.
The path to the location where the backup files created. The default path is the backup directory in the SecureAnyBox installation directory. By default: /opt/tdp/secureanybox/backup or C:\SecureAnyBox\backup
A time stamp in the rrrr-mm-dd format is automatically added after the prefix (e.g., secureanybox-backup-2018-05-17.zip). The default prefix is secureanybox-backup.
The number of maintained backups. Backup is done every day at midnight. When a count of backups exceeds the number set here, the oldest backups automatically deleted. The default number of backups is 7.
Allows you to edit the default user rights of the backup file.
User account which will be set as the owner when creating the backup file (e.g., root, Administrators).
This field displayed if SecureAnyBox server runs on Windows platform
Group of users with permissions to backup files.
This field displayed if SecureAnyBox server runs on Linux platform
Permissions that are set to backup files. The Unix symbolic notation in the rw-rw--— format is used for the setting (see https://en.wikipedia.org/wiki/File_system_permissions). By default, only the owner has permission to read and write (rw-------).
This field displayed if SecureAnyBox server runs on Linux platform
Table with information about backups displays below the backup configuration details.
The LDAP connector holds LDAP server connection settings used for communication with the LDAP server to synchronize users from LDAP to the SecureAnyBox, and vice versa. Three types of Directory services are supported – eDirectory, Active Directory, and generic LDAP.
For each connector, it is possible to set more than one LDAP server for backup or load balancing purposes. All servers set to one connector need to be the same type (eDirectory, Active Directory, or generic LDAP).

By clicking the
sync
button, a user starts manual synchronization with the LDAP server. User is also redirected to the
LDAP synchronization log page, where is possible to see synchronization results.
By clicking the
view
button, a user is redirected to the
LDAP Viewer page, where he can view which users can be synchronized from the LDAP server after filtration specified in the LDAP connector is applied.
To create a new LDAP connector, click on the add LDAP Connector button and wait for a form to display.

Unique connector identifier. Connector ID must start with a letter and contain only letters, numbers and underscore.
Uncheck (false) to disable this connector.
LDAP server type.
LDAP server address or addresses of multiple LDAP servers with same directory replica/mirror (for failover).
To add an LDAP server, click on the button with the plus symbol and wait for a form to display.

In a form, enter the
Server address
and
Port
of LDAP server. The server address can be entered as an IP address (e.g.,“172.22.13.1”) or as a domain name (e.g.,“ldapsrv.tdp.cz”). Port is set to 636 by default along with using the
SSL
.
We recommend using the SSL protocol to communicate between SecureAnyBox and LDAP server.
To successfully add new LDAP server address, confirm entered values by clicking on the
OK
button.
Server address
Please enter LDAP server address. Server address can be entered as an IP address (e.g. “172.22.13.1”) or as a domain name (e.g. “ldapsrv.tdp.cz”)
Port
Port on which SecureAnyBox communicates with LDAP server. For connection with SSL protocol is used port 636 and for connection without SSL protocol is used port 389.
SSL
Enable/disable SSL protocol during communication between SecureAnyBox and LDAP server. We strongly recommend using SSL protocol.
When enabled, LDAP requests will be distributed among available LDAP servers (for load balancing). When not enabled, SecureAnyBox will connect to the first server available. Servers are tried in the order in which they are defined.
LDAP User DN used by SecureAnyBox to access LDAP directory, lookup users, change passwords, etc.
Minimum access rights:
entry/object rights – browse
cn – read, compare
objectClass – read,compare
Use
Create SecureAnyBox objects
button to create manager user automatically when using NetIQ (Novell) eDirectory. If you are connecting to a directory service from another vendor, create a manager user using your directory service management console. LDAP interface on some directory services (e.g.,Active Directory) doesn’t provide access rights/permissions modification...
e.g.,cn=secureanyboxmgr,o=org or cn=secureanyboxmgr,cn=Users,dc=DOMAIN,dc=local
LDAP container used as a search base for LDAP synchronization search query. When the search base not set, the search starts at the root of the LDAP tree.
e.g.,o=org or leave empty to search from the root of the tree
Uncheck to search only the immediate subordinates of the specified search base.
An alias is an entry which points to another object in the namespace – by containing its dn. Searching the entry that an alias entry points to is known as dereferencing an alias.
There are four modes of dereferencing aliases:
When set to greater than zero, SecureAnyBox will use Simple Paged Result extended control to retrieve LDAP search results in pages of a given number of entries. Some LDAP servers have a default server-side limit for a number of entries returned in the single response. For example, Active Directory servers have a default limit of 1000 objects for a single search request. Setting Search Page Size to 1000 or lower will allow SecureAnyBox to retrieve more results (than the server limit) using multiple requests. When set to 0 no paging is used, and an only single request is used to retrieve all results. This setting is used when importing users and in LDAP Viewer.
When using embedded LDAP from KeyShield SSO, this value must be set to 0.
List of FDNs included in user synchronization.
List of FDNs excluded from user synchronization.
e.g.,(objectClass=person)
A number of LDAP connections SecureAnyBox will keep alive to improve the performance of LDAP requests.
LDAP attribute used by LDAP authentication for user lookup. Referred to as uid in ldap synchronization log.
LDAP attribute used as UUID (Universally unique identifier) attribute. This attribute value is used to uniquely identify the user object in LDAP directory and must be unique across domains and LDAP connector. Usually, GUID (eDirectory) or objectGUID (Active Directory) LDAP attributes are used and recommended, because they are generated to be unique globally.
LDAP attribute used as a first name.
LDAP attribute used as a middle name.
LDAP attribute used as a surname.
Enable mapping to Display name
Field is displayed only if the Display Name Mapping field is checked.
LDAP attribute used as a display name.
Enable mapping to Short display name
Field is displayed only if the Short Display Name Mapping field is checked.
LDAP attribute used as a short display name.
You can set source LDAP attribute for reading user e-mail address and optional regex to pick correct e-mail address if source attribute is multi-valued.
Fields below are displayed only if the Custom Mail Attribute field is checked.
Source LDAP attribute used to read user e-mail address.
Mapping method used to read e-mail value, for example, when the source attribute is multivalue. The default mapping method (First value) reads the first value of the attribute as is returned by the server.
This field is displayed only if the Mapping method field is set as First match or First match or first value.
Regular expression used to find the value of the user’s e-mail address. For example use regex .*@yourdomain.com to match e-mail address from yourdomain.com.
Synchronized user objects are created in this domain.
Enable periodic synchronization of users from LDAP connector.
The delay between the synchronization of LDAP users from this connector.
To complete the configuration of the LDAP connector, please confirm the form by clicking the OK button. The application must be restarted for the LDAP connector to function properly.
While configuring new eDirectory LDAP connector, you can click on the Create SecureAnyBox objects button, to proceed eDirectory installation directly from SecureAnyBox web interface. After clicking on the button wait for the eDirectory Installation form to displays.

LDAP server address. The address can be specified in various formats (e.g. 172.22.40.68, localhost, mail.tdp.cz), but cannot be specified along with the type of connection (e.g. smtp://127.0.0.1).
The port on which SecureAnyBox communicates with the LDAP server. For SSL connection, use port 636 and for SSL-free connections use port 389.
Enable/disable the use of SSL for communication between SecureAnyBox and LDAP. We strongly recommend using SSL.
LDAP container used as a search base for LDAP synchronization search query. When the search base not set, the search starts at the root of the LDAP tree.
e.g.,o=org or leave empty to search from the root of the tree
LDAP container where SecureAnyBox objects (like a SecureAnyBox manager) should create.
Enter FDN of LDAP admin (e.g.,cn=admin,o=org). LDAP admin credentials are necessary to create SecureAnyBox objects in LDAP.
Enter admin password
When enabled, you can override User DN and password for SecureAnyBox mgr user. Otherwise will be used default values.
LDAP User DN used by SecureAnyBox to access LDAP directory.
Password pattern for generating a SecureAnyBox manager password. Each letter in the pattern corresponds to letter in the generated password.
See examples of the password pattern
Characters allowed in the password pattern and their meaning:
v – lowercase vowel a,e,i,o,u,y
V – mixed case vowel (A,E,I,O,U,Y,a,e,i,o,u,y)
Z – upper case vowel
c – lowercase consonant (b,c,d,f,g,h,j,k,l,m,n,p,q,r,s,t,v,w,x,z)
C – mixed case consonant
z – upper case consonant
l - any alphabet character (vowel or consonant) - lowercase
A - any alphabet character - mixed case
u – upper case alphabet
d - digit (0-9)
s – special character (.,@,&,*,(,),<,>,_,],[,%,$,#,\,/,?,;,-,:)
n – digit or special character
\ - escape character - next character is used as is (e.g pattern ‘\-‘ outputs ‘-‘ in the resulting password)
* - any allowed character
Default pattern is CVCVdddCVCCVdC (this might generate passwords such as “wEHe063heFme4p”).
For example, you can set a password pattern as “\p\a\s\sddddddd” and this might generate password such as “pass1762885” or “pass5687412”.
Please set SecureAnyBox manager password. The password can be generated by clicking on the Generate button. Generated passwords are safer and don’t have any link to a person who made them (like a pet’s name, favorite actor or nickname). Generated passwords are formatted by the current password pattern. Generated passwords can also be edited.
Once all required values set, click on the OK button and wait until the installation process successfully. If no error occurs, eDirectory Installation form is no longer displayed, and in the LDAP connector form is displayed a message Success.

In this part of SecureAnyBox configuration, you can set integration with the KeyShield SSO. SecureAnyBox support two types of Keyshield authentication – by IP address and by certificate using Client API.

KeyShield SSO integration for clients with the unique IP address using KeyShield SSO web REST API.
KeyShield SSO authentication is disabled by default. You can enable it for all users or non-admin users only.
KeyShield SSO server URL (syntax: http://address:port).
If you are connecting to Keyshield SSO server using SSL (via HTTPS instead of HTTP), you need to import a certificate from KeyShield SSO server to your Java Keystore. More...
KeyShield SSO server URL (syntax: http://address:port).
If you are connecting to Keyshield SSO server using SSL (via HTTPS instead of HTTP), you need to import a certificate from KeyShield SSO server to your Java Keystore. More...
http://127.0.0.1:8485
Key used to authenticate against KeyShield SSO API. To obtain the API key, go to the KeyShield SSO Administration.
When SecureAnyBox is behind a reverse proxy server, it is necessary to enter the trusted proxy IP address (or multiple addresses) to enable KeyShield SSO integration.
Determines the timeout in seconds until a connection to KeyShield SSO server established.
Select the authentication type. This value determines, whether the authentication through login form enabled, or whether the two-factor authentication used.
Copy this URL and use it in notification configuration within KeyShield SSO Server.
Integration with Keyshield SSO for clients with the non-unique IP address. This authentication uses KeyShield SSO client API and requires browser extension to work. Using KeyShield SSO (Windows) client in TLS mode is also required.
Enables SSO through KeyShield SSO Client API
Upload KeyShield SSO API certificate which can be downloaded from KeyShield SSO configuration in the API section.
Configuration of Default password pattern, which is used in Safe Boxes and Records, offering of previously entered labels, maximum file size, policy of the Access Code and applying of permission templates.

Default password pattern for Safe Boxes and Records where no password pattern set.
Each letter in the pattern corresponds to letter in the generated password.
See examples of the password pattern
Characters allowed in the password pattern and their meaning:
v – lowercase vowel a,e,i,o,u,y
V – mixed case vowel (A,E,I,O,U,Y,a,e,i,o,u,y)
Z – upper case vowel
c – lowercase consonant (b,c,d,f,g,h,j,k,l,m,n,p,q,r,s,t,v,w,x,z)
C – mixed case consonant
z – upper case consonant
l - any alphabet character (vowel or consonant) - lowercase
A - any alphabet character - mixed case
u – upper case alphabet
d - digit (0-9)
s – special character (.,@,&,*,(,),<,>,_,],[,%,$,#,\,/,?,;,-,:)
n – digit or special character
\ - escape character - next character is used as is (e.g.,pattern ‘\-‘ outputs ‘-‘ in the resulting password)
* - any allowed character
Default pattern is CVCVdddCVCCVdC (this might generate passwords such as: wEHe063heFme4p).
For example, you can set a password pattern as ‘\p\a\s\sddddddd‘ and this might generate passwords such as ‘pass1762885‘ or ‘pass5687412‘.
Selection of which data displays in the middle column of the list of records in the Safe Box – after the record name. The default value is
Description.
This value is set for the server and can be overridden in the domain and the user preferences.
When entering a tag in the record’s form, previously typed tags will not offer.
This value determines the maximum size of the file which is possible to store in a record (file or certificate type of record).
Sets whether the user who has delete permission for Safe Box can delete the Safe Box or only content inside.

Minimum length of the access code.
Minimum number of uppercase letters in Access Code.
Minimum number of lowercase letters in Access Code.
Minimum number of digits in Access Code.
Minimum number of special characters in Access Code.
By setting the Access Code Timeout, you will enable temporary remembering of the Access Code. The last entered valid Access Code will be temporarily stored in a cache (for the specified amount of time), so users will not have to enter the Access Code repeatedly.
To turn this feature off, set the Access Code Timeout to 0.
User Access Code is temporarily disabled after this number of unsuccessful attempts. Set to 0 to turn this feature off.
User cannot use his/her access code for this amount of minutes
| Default value | Minimum value | |
|---|---|---|
| Minimum length | 8 | 5 |
| Uppercase letters | 1 | 0 |
| Lowercase letters | 1 | 0 |
| Digits | 3 | 0 |
| Special characters | 0 | 0 |
| Minimum Entropy | 20 | 0 |
Configuration of e-mail notifications. Notifications will be sent when some user makes changes in the records (Safe Boxes, Accounts and so on).

Please enter the SMTP server address from which notification emails will send. The host address can be specified in various formats (e.g. 172.22.40.68, localhost, mail.tdp.cz), but cannot be specified along with the type of connection (e.g. smtp://127.0.0.1).
Please enter the port of the SMTP server. Usual SMTP ports are 25, 587 or 2525.
Please enter a username of SMTP account which the SecureAnyBox will be using to connect to the SMTP server.
Please enter a password for SMTP account which the SecureAnyBox will be using to connect to the SMTP server.
Enter an e-mail address from which the notification emails will send.
By enabling the e-mail notification, you will allow sending notification emails with a summary of changes in the records.
When the notifications enabled, it is possible to set options when and to whom the emails will be send.
If this field checked or the value is “yes” notification emails will be sent only if some encrypted fields (in records) changes.
If this field checked or the value is “yes” notification emails will send only to watchers of Safe Box in which the changed record stored.
If this field checked or the value is “yes” notification email will send even to the user who made changes.
Set the time (in minutes), during which the SecureAnyBox will aggregate changes. After the set time, SecureAnyBox will send an e-mail with the summary of all changes in the record.
Configuration of external files. External files are encrypted by SecureAnyBox and stored on another server. In this part of the Configuration, it is possible to set default external files path.

Create domain Edit domain Disable domain Delete domain Show Domain Users
The page intended to manage domains. Only users with a role User Manager or Administrator have access on this page.
Domains can be used to divide a SecureAnyBox into several parts. Each domain has its users management and it is possible to create a hierarchical structure of domains.
The structure of domains can copy the structure of your company, and it is possible to create a hierarchy by setting the visibility of one domain for other domains, which are on the higher spot in a company structure.
For example, here can be created two domains named "Management" and "Technical support". Because users of the domain "Management" have a higher position in the structure of the company, the domain "Technical Support" will be set as a visible for users of the domain "Management".
This setting allows the domain users "Management" to grant access to Safe Boxes to users of both domains, but users of the domain "Technical support" can grant access to Safe Boxes only to users of their domain.
Domains can also copy the structure of containers in LDAP. When setting an LDAP connector is required to select the domain, into which users will import from that connector. Each LDAP connector can have only one domain.
Only users with a role Administrator from System domain can create a domain. Users with a role User Manager can only edit their domain.
To create a domain click on the New Domain button at the Domain page. After clicking on the button, the domain’s form displays.

All fields are going to display after entering a domain name.
When enabled, users from this domain can log in.
The name should characterize the domain. Each domain name must be unique.
If more than one domain is specified, it will be required to fill the domain name at the login page.
By clicking on the Login page link button, is possible to get a link to the login page, where the domain name will be prefilled.
The description should more specifically characterize the domain.
If this limit reached, non-initialized users will not be able to set the access code.
Select a language which users of this domain will have set by default. The language can be changed anytime.
List of domains visible for users of this domain.
Users of this domain can share their Safe Boxes and Safe Box Groups also with users of visible domains.
Agent Configurations assigned to this domain.
When the agent configuration assigned, users with a role Administrator can modify or remove agent configuration. Administrators from other domains (if the agent configuration is visible for them) can copy agent configuration only.
Assigned Agent Configuration is visible to users from this domain by default. To modify the visibility of agent configuration, go to the Agent configuration settings.
If the Agent Configuration is visible to the user with access to the stations and their passwords, the agent configuration can be selected while registering stations or obtaining passwords.
Agent Configuration can be assigned to one domain only.
After manually create a user who does not have a password, send this user an invitation e-mail with a link to set the password.
Use of second factor (authenticator application) is either optional – enabled by user in the top right menu, or mandatory.

Default password pattern for Safe Boxes and Records which will create in the domain, where no password pattern set.
Each letter in the pattern corresponds to letter in the generated password.
See examples of the password pattern
Characters allowed in the password pattern and their meaning:
v – lowercase vowel a,e,i,o,u,y
V – mixed case vowel (A,E,I,O,U,Y,a,e,i,o,u,y)
Z – upper case vowel
c – lowercase consonant (b,c,d,f,g,h,j,k,l,m,n,p,q,r,s,t,v,w,x,z)
C – mixed case consonant
z – upper case consonant
l - any alphabet character (vowel or consonant) - lowercase
A - any alphabet character - mixed case
u – upper case alphabet
d - digit (0-9)
s – special character (.,@,&,*,(,),<,>,_,],[,%,$,#,\,/,?,;,-,:)
n – digit or special character
\ - escape character - next character is used as is (e.g.,pattern ‘\-‘ outputs ‘-‘ in the resulting password)
* - any allowed character
Default pattern is CVCVdddCVCCVdC (this might generate passwords such as: wEHe063heFme4p )
For example, you can set password pattern as ‘\p\a\s\sddddddd‘ and this might generate password such as ‘pass1762885‘ or ‘pass5687412‘.
Selection of which data displays in the middle column of the list of records in the Safe Box – after the record name. The default value in server configuration is
Description.
This value is set for the domain and can be overridden in the user preferences.
Choose a default Safe Box type for all new Safe Boxes and Safe Box Groups which will be created in this domain.
Shared – Access rights are inherited from parent level.
Private – Blocks access rights inheritance from parent level.
Check this box to override the maximum file size. The default value is 15 MB.
This value determines the maximum size of file which is possible to store in a record (file or certificate type of record).
Enables/ Disables sharing of permissions for Safe Boxes to other users
Checking this box will override ‘Access Code Timeout’ settings, and for users of this domain, the access code will not be remembered.
For Safe Box Groups, Safe Boxes, and records users from this domain create or obtain access will be set the watching of changes automatically by default.
Each user can change whether changes will be watched automatically in the user preferences form.
If sending notifications is enabled (in the server configuration), e-mail notifications will be sent with a summary of changes to the watched ones.
For Safe Box Groups, Safe Boxes, and records users from this domain create or obtain access will have set the watching of accesses to encrypted information automatically by default.
Each user can change whether accesses to encrypted information will be watched automatically in the user preferences form.
If sending notifications is enabled (in the server configuration), e-mail notifications will be sent with a summary of accesses to encrypted information to the watched ones.


By overriding the Login Password Policy, you can set the policy only for this domain. If not override, login password policy from the Configuration (if specified) will apply.
Fields below are displayed only if the Override Password Policy field is checked.
Minimum length of the login password.
Minimum number of uppercase letters in login password.
Minimum number of lowercase letters in login password.
Minimum number of digits in login password.
Minimum number of special characters in login password.

By overriding the Access Code Policy, you can set the policy only for this domain. If not override, the Access Code Policy from the Configuration will apply.
Fields below are displayed only if the Override Access Code Policy field is checked.
Minimum length of the access code.
Minimum number of uppercase letters in Access Code.
Minimum number of lowercase letters in Access Code.
Minimum number of digits in Access Code.
Minimum number of special characters in Access Code.

The number of Security Officers required to open White Envelope. Count of configured Security Officers has to be greater than this.
If this limit reached, non-initialized users will not be able to set the access code.
Number of Security Officers appointed in your organization. SecureAnyBox will warn you if the Security Officer Count falls below this value.
These settings of Default Safe Box permissions are used as default settings of permissions while creating a new user into the domain.

By checking the fields below, new users created (not updated during LDAP synchronization) in this domain will be granted access to licensed features – CBT client (Custom Branded Trusted client) or File manager plugin. A number of users with access to Licensed features cannot exceed the number of licenses.

CBT (Custom Branded Trusted) client is a native Windows application simplifying work with SecureAnyBox file records. For more information, contact your distributor .
File Manager plugin for Total Commander or FAR allows working with Safe Boxes and records in them from these applications.
To edit a domain, click on the row in a list of domains. After clicking, the domain form will display. In the form can be changed any value.
To apply changes, click on the
OK
button.
By clicking on the
Cancel
button, all changes will revert.
By disabling a domain, you can block login of all users in the domain. To disable the domain, open domain’s form by clicking on the row in a list of domains and uncheck the
Enabled
field. After saving, the domain is disabled.
The domain which was disabled can be enabled anytime.
The domain can be deleted only if it does not contain users. To delete the domain, click on the cross icon (
![]() ) at the end of a row in a table of domains.
) at the end of a row in a table of domains.
Deleting the domain have to be confirmed.

It is possible to view users from a specific domain by clicking the appropriate icon (
![]() ) in the domain table. After clicking the icon, a list of users of the domain will show in the new tab.
) in the domain table. After clicking the icon, a list of users of the domain will show in the new tab.

Create user Edit user Disable user Enable user Unban user Export a list of users Delete user Invite user Send message Move user
The Users page is intended for the users management. Only users with a role User Manager have access to this page.
Users are filtered by domain by default. To change a domain by which users are filtered, click on the Select domain button and in a list of domains choose a domain whose users should be displayed. It is possible to have displayed all users from all domains by clicking on the All Domains in a list of domains.

Users can be created manually or can be imported from LDAP.
Before creating a new user is important to select the domain into which a user will create.
To create a new user, click the New User button. After clicking on the button, a user form displays.

Fields
Security Officer
(
![]() ) and
Inherited
(
) and
Inherited
(
![]() ) can be edited after the new user sets an access code.
) can be edited after the new user sets an access code.
A domain in which the user belongs.
To change the domain into which a new user created, you must select a different domain on the Users page.
Once the user created, it is possible to move the user to a different domain.
Username which the user will use to log in.
By clicking on the
Login page link
button, it is possible to get a link to the login page, where the domain name and the username will pre-fill.
Once the user created, this value cannot be changed.
When the field is checked (or a value of this field is “yes”), the user will be synchronized with LDAP.
Once the user created, this value cannot be changed.
Set a password. When the password is not set, the user cannot log in.
User password.
While entering the password, there is shown how long the password is, how many lowercase and uppercase letters, numbers, and other symbols it contains and how much secure the password is.
The password will be displayed after clicking on the eye icon behind this field.
Repeat the password
Enables/disables user account login.
Select a language that the user will use in the application. The language can be changed anytime.
By checking the fields below, the user will be granted access to licensed features – CBT client (Custom Branded trusted client) or File manager plugin.
CBT (Custom Branded Trusted) client is a native Windows application simplifying work with SecureAnyBox file records. For more information, please contact your distributor.
File Manager plugin for Total Commander or FAR allows working with Safe Boxes and records in them from these applications.
This part of the form is displayed if the user is synchronized with LDAP
User GUID (entryUUID or objectGUID) used to match user with LDAP object during LDAP synchronization (hexadecimal format in lowercase e.g.,950aea900084d311aef800e029255247). Use LDAP Viewer to get user GUID in the correct format if you for some reason need to link existing user record with LDAP.
Name of the LDAP connector with which the user is synchronized.
LDAP user DN (distinguished name).
| User role | Description |
|---|---|
| Administrator | User administers SecureAnyBox server configuration – domains, URLs, LDAP, SSO, email, SIEM, diagnostic logs, etc. |
| Auditor | User is approved to access the complete audit log through a set of reporting tools. This doesn’t include any access to the encrypted data. |
| SecureAnyBox User | User is generally allowed to get passwords managed by agents, can be limited by access rights. |
| SecureAnyBox Admin | User is approved to administer configuration of agents. |
| User Manager | User is approved to manage domains, user accounts, assign roles and default rights. |
| Security Officer | User, only together with other Security Officers, can open White Envelopes within his/her domain |
| Safe Boxes User | User is allowed to use SafeBoxes (must have valid Access Code) |
The user role also determines to which parts of SecureAnyBox the user have access to and what actions he can perform. A basic overview of what actions and parts of SecureAnyBox are accessible for a user with specific user role is in the table below.
| User role | SecureAnyBox | Safe Boxes | Reports | Audit | Administration | |
|---|---|---|---|---|---|---|
| Administrator | Access | yes | yes | yes | no | yes |
| Extra access | Access to Agent Configuration, Configuration. Only Administrator has access to them | |||||
| Auditor | Access | no | no | no | yes | no |
| Note | The auditor who belongs to System domain can do an audit over all domains | |||||
| SecureAnyBox User | Access | yes | no | no | no | no |
| Actions | View registered stations, obtain passwords for stations | |||||
| SecureAnyBox Admin | Access | yes | no | no | no | no |
| Actions | All actions with stations, tickets, passwords | |||||
| User manager | Access | no | no | no | no | yes |
| Actions | View and edit domains and all actions with users | |||||
| Security Officer | Access | no | yes | yes | no | no |
| Actions | Can open White Envelopes of other users (in co-op with other Security Officers) | |||||
| Safe Box User | Access | no | yes | yes | no | no |
| Actions | Can use Safe Boxes | |||||
When setting up a user role, other roles can be automatically set to the user too. It happens if user role includes all features of another role.
For example, user role
Administrator includes all features of
SecureAnyBox User,
SecureAnyBox Admin, and
User Manager user roles and even some extra features (access to the Configuration and can create a domain). So when user has an
Administrator user role, he also has
SecureAnyBox User,
SecureAnyBox Admin, and
User Manager user roles.
To edit the user, click the user’s name in a list of users. After clicking, a user details displays.
If the user is imported from LDAP, different fields display in a user detail.

User can be also edited from the user’s action menu. To open the action menu, click on three dots (
![]() ) in the
Actions
column. After clicking, action menu appears, where it is necessary to click on the
Edit
.
) in the
Actions
column. After clicking, action menu appears, where it is necessary to click on the
Edit
.

After changes finished, confirm them by clicking the OK button in the user details form. Depending on changes, you can be asked to enter the access code. Have you forgotten the access code?
If you only want to prevent the user from login to SecureAnyBox, you can disable the user’s account. Once disabled, the user cannot access SecureAnyBox, but all his records are still stored. Unlike deleting, this action can be taken back anytime.
To disable the user, uncheck
Enable
field in user details form.

User can be also enabled from the user’s actions menu. To open the action menu, click on three dots (
![]() ) in the
Actions
column. After clicking, action menu appears, where it is necessary to click on the
Disable
.
) in the
Actions
column. After clicking, action menu appears, where it is necessary to click on the
Disable
.

It’s also possible to disable multiple users at one time. Please check all users which should be disabled and click on the Disable button. After clicking, all selected users are disabled.

The user must be enabled, to be able to log in to SecureAnyBox. To enable the individual user, check the Enabled field in the user details form.

User can be also enabled from the user’s action menu. To open the action menu, click on three dots (
![]() ) in the
Actions
column. After clicking, action menu appears, where it is necessary to click on the
Enable
.
) in the
Actions
column. After clicking, action menu appears, where it is necessary to click on the
Enable
.

It is also possible to enable multiple users at once. Please select all users to be enabled and click the Enable button. After clicking, all selected users will be enabled.

If the user enters access code or login password incorrectly for many times, then the user is temporarily banned to enter the access code or to login. Banned users have an icon with a red lock in the list of users.
![]() - Built-in administrator account, login is banned.
- Built-in administrator account, login is banned.
![]() - Manually created user, login is banned.
- Manually created user, login is banned.
![]() - User is disabled, login is banned.
- User is disabled, login is banned.
![]() - Synchronized from LDAP connector, login is banned.
- Synchronized from LDAP connector, login is banned.
![]() - Access code entry is temporarily banned because it was entered incorrectly several times.
- Access code entry is temporarily banned because it was entered incorrectly several times.
The number of unsuccessful attempts of entering the access code or the login password, and how long the user is banned, is set in the Configuration.
To unban banned users, select all users to be unbanned and click the Unban button.

At the Users page, it is possible to filter displayed users by checking/unchecking filter fields (
![]() ). The filtered list of users is possible to export in CSV format by clicking on the
Export to CSV
button.
). The filtered list of users is possible to export in CSV format by clicking on the
Export to CSV
button.

Into a file are exported values displayed in a list of users (name, username, email, domain, LDAP connector and roles).
User can be deleted from the user’s action menu. To open the action menu, click on three dots (
![]() ) in the
Actions
column. After clicking, action menu appears, where it is necessary to click on the
Delete
.
) in the
Actions
column. After clicking, action menu appears, where it is necessary to click on the
Delete
.

If the user is the only one, who has permissions for some Safe Box, the Safe Box will be deleted with the user. If you don’t want to delete the Safe Boxes, assign permissions for these Safe Boxes to a different user.

After users created, you can send them an e-mail invitation to SecureAnyBox. In the invitation will be a link to set the password. Once the password is set, the user can log in and set the access code.
To send invitations to users, select (by checking) users you want to invite to the SecureAnyBox and click the Invite users button.
To send the invitations, you have to configure mail server in the Configuration first.

User can be also invited from the user’s action menu. To open the action menu, click on three dots (
![]() ) in the
Actions
column. After clicking, action menu appears, where it is necessary to click on the
Invitation
.
) in the
Actions
column. After clicking, action menu appears, where it is necessary to click on the
Invitation
.

After clicking Invitation in the user’s actions menu, the dialog Invitation displays. If the user has set e-mail address, you can create and send invitation to user’s e-mail or you can create invitation without sending it.

If the invitation is only created and does not have been sent, in the invitation dialog appears an invitation link which is possible to copy to clipboard.

If users have an email address specified, you can send them a message from SecureAnyBox.
To send a message to users, select (by checking) users you want to send a message and click the
Send message
button.

To send the messages, you have to configure mail server in the Configuration first.
After clicking the Send message button, a window for entering message text displays. To send a message, click the Ok button.

Users can be moved between the domains. To move users, select all users which should be moved and click on the Move button.
Moved user lose all inherited permissions to Safe Boxes. All assigned permissions stay valid.

After clicking on the button, a list of domains into which you can move selected users displays. Please select a domain into which selected users move, by clicking the domain name.
The move of users has to be confirmed.

Only users with a role User Manager have access to this page.
User tags intended for easier management of users and their permissions. To each domain, it is possible to assign an unlimited number of tags. User tags can be added to users with same domain only.
User tag can be assigned to:
User tag is used to create a Permission template for users who have the user tag assigned.

Only users with a role Administrator have access to this page.
LDAP Viewer allows you to browse the LDAP tree of any of configured LDAP connectors. LDAP Viewer uses the “SecureAnyBox manager” account defined within the selected LDAP connector configuration. This means, that LDAP objects and their attributes you see with the LDAP Viewer correspond to what the selected authentication connector ‘sees’. If you don’t see what you expect (a specific user object or its attributes), then the access rights of the “SecureAnyBox manager” account for the particular LDAP tree are not sufficient. Please check the access rights assigned to the search base or root of the LDAP tree as well as possible inheritance filters.
To use LDAP viewer is necessary to configure at least one LDAP connector. After opening the page, a list of LDAP connectors displays. By clicking the connector name, you can view objects in a search base (as configured in the LDAP connector).

Displayed objects are folders (containers) and users. Click the folder name to view users and folders inside the folder. Click the username to view details about the user.

It is possible to filter the displayed objects by entering their name in the search field above the table. Should you need filter the displayed objects by LDAP search expression, click the Lookup object(s) button and use the filter field instead.

Only users with a role Administrator have access to this pages.
In the Logs part of the application, it is possible to see diagnostic log or LDAP synchronization log. Different log levels in displayed messages are visually distinqished:
| Log levels: |
|
INFO |
|
WARNING |
|
DEBUG |
|
ERROR |
On the Diagnostic log page a current log is automatically displayed.

The current log can be refreshed manually by clicking on the
Refresh
button or automatically by clicking on the
Enable autorefresh
button. Automatic refresh of the log is possible to turn off by clicking on the
Disable autorefresh
button.
To change a log level or log browser line limit, click on the
Configure logging
. After changes are confirmed, it is necessary to restart the SecureAnyBox for applying the changes.
To download the current log, click on the button
Download
and confirm the download.
If you need older than current log, click on the
Logs
button to display a list of available logs.

In the first table are displayed application logs for each day. To download the log, click on the log file name and confirm the download.
On the LDAP sync log page, is displayed a table with names of specified LDAP Connectors. Click on the connector name to view details of the last synchronization with LDAP.

The synchronization log can be refreshed manually by clicking on the
Refresh
button or automatically by clicking on the
Enable autorefresh
button. Automatic refresh of the synchronization log is possible to turn off by clicking on the
Disable autorefresh
button.
Synchronization of users can be started manually by clicking on the
Synchronize
button.
Settings of the synchronization can be changed anytime by clicking on the
Configure <LDAP connector name>
button.
To download the log of the last synchronization, click on the button
Download
and confirm the download.
To filter skipped users during the synchronization with LDAP, click on the button
Show only skipped users
.

Server status page intended for displaying problems with SecureAnyBox server. If any error or warning occurs, users will be warned by the number of errors and/or warnings in the top right corner of the page.

|
On the SecureAnyBox server occurred 1 error, and 2 warnings |

|
On the SecureAnyBox server occurred 1 warning |

|
On the SecureAnyBox server occurred 1 error |
After clicking on the number of errors and/or warnings, the Server status page loads. On the Server status page are shown three sections – Server Messages, Station registrations, and White Envelopes. In accordance with the user’s role, the SecureAnyBox determines which sections will display.
| Section | User role | ||||
| Administrator | User manager | SecureAnyBox Admin | Security Officer | other roles | |
| Server Messages | yes | no | no | no | no |
| Station Registrations | yes | no | yes | no | no |
| White Envelopes | yes | no | no | yes | yes |
Server messages section displays only to the user with role Administrator. To handle messages from this section, go to the Configuration page.

Station registration section displays only to the user with role SecureAnyBox Admin. To handle messages from this section, go to the SecureAnyBox part of the application.

White Envelopes section displays only to the user with role User manager, and Security Officers

On the License page, users can see information about the currently used licenses. Users can check a number of remaining licenses for Safe Boxes, Safe Box Groups, records, users, domains, applications, etc.

Manually created users can be synced with the LDAP server additionally, without losing saved data. It is possible to associate a user with an existing LDAP account or create a new LDAP account.
To synchronize a user with LDAP, the user must pass these conditions:
We also recommend setting the username in SecureAnyBox same as username (UID) in LDAP.
During the synchronization, the users' information should be updated according to information in LDAP and fields LDAP connector, and LDAP DN should fill. Otherwise, synchronization was unsuccessful and please refer to the log of synchronization.
To see the log of synchronization go to
Administration > Logs > Logs and click the LDAP connector name in Synchronization table. At the synchronization log page, you can view a log of the last synchronization with LDAP connector, start synchronization and open configuration of LDAP connector.
All issues that occurred during the synchronization have the WARNING logging level and have yellow coloring.
While entering the GUID into manually created user details, an error message that the GUID not unique appears.

A user account may have been already imported from LDAP to SecureAnyBox. You can search users by GUID on the Users management page. A user with the same GUID can even be in another domain. To search for users in all domains, please click the
Find users button.
In a case, the user already imported from LDAP, please delete the imported account. Then enter the GUID into user details of the user who should be synchronized with LDAP and run the synchronization with LDAP.
To determine the cause of the failure, please go to the synchronization log page and enter the username of the synchronized user in the search field.

Possible situations:
Example:
existing user with uid=‘peter’ (but different UUID) found in database -> skipping cn=peter,o=org
A user with the username “peter” is manually created and should be synchronized with LDAP. However, the user account in LDAP has a different GUID (UUID) than the user in SecureAnyBox. To successfully synchronize “peter” with LDAP, you need to modify the GUID according to UUID in LDAP.
Example:
existing user ‘mbriggs’ cannot be renamed to ‘monica’ username not unique -> skipping cn=monica,o=org
The user with username “mbriggs” is manually created and should synchronize with LDAP. In LDAP, the user with the same GUID (UUID) has different UID - “monica”. During the synchronization, SecureAnyBox tries to change username “mbriggs” to “monica”, so the username will be the same as is UID in LDAP. To successfully synchronize the user “mbriggs” with LDAP, it is necessary to edit or delete the user with username “monica”.
Linux Standard Base (lsb) must be installed, otherwise, the SecureAnyBox can’t register for automatic start. Linux Standard Base is available through various online repositories.
The installation procedure depends on your distribution, it can be for example sudo yum install redhat-lsb-core for SUSE/RedHat/CentOS Linux(rpm based) or sudo apt-get install lsb-core for Ubuntu Linux, Debian (deb package based distributions).
On some Linux distributions (e.g. Open SUSE) it is also necessary to install insserv-compat package to enable init scripts and start SecureAnyBox automatically (for more information, please refer to this page).
If you decide not to install LSB or it is not available for your system, you still can register the starting script manually. We always create it in /etc/init.d/
We don’t support other JVMs than Oracle Java. You can install Oracle JVM manually, locate and use existing installation or choose private Oracle JVM installation. Tested and approved Oracle JVM is always a part of the installation package,just choose the Private Java option when you start the installation script.
The default installation path is /opt/tdp/secureanybox, but you can choose whatever path/device you need.
Installation script then needs the IP address and port - this can be changed later, but you have to choose address:port combination which will not cause any conflict with other services running on the box. Thus we recommend starting with the default port. Once you enter the management console, you can change it or add more interfaces on a different address:port combinations. If a conflict will be detected, the system reverts to the last “good” configuration which allows you to continue.
It is highly recommended to switch to SSL (https) as soon as possible. You can use a built-in function for generating a self-signed certificate, or you can import your existing certificate with a private key (usually available in PKCS12 format). Please keep in mind, that interfaces are virtualized - it is necessary to set both IP address and URL otherwise system is not able to accept a request.
Please note – export limitations does not allow to distribute JVM with unlimited encryption policies. You can download and apply unlimited encryption policies if it is legal in your country ( please refer to www.oracle.com for detailed information). You can’t use a password longer than 7 characters without application of unlimited policies.
In a case of upgrading the SecureAnyBox, the same installation script is used. Please confirm the same installation path like before and choose the default option NOT to overwrite the configuration file.
SecureAnyBox upgrade is provided by the installation script which is a part of the new release package downloaded from the website. Download the .bin package from the Downloads section at www.secureanybox.com. Then start the installation by ./inst_secureanybox…

If your installation is standard with the embedded Oracle Java (recommended), answer No.

Then the script gets the path used for the previous installation and offers it as default. Confirm this path because this is an upgrade and the goal is to upgrade the existing installation – running instance.

The configuration.properties file must be preserved to upgrade the running system.
Confirm default answer N = not to overwrite

Now you are ready to start the new installed release – it will stop SecureAnyBox and rerun it. Once the new release is running, it will convert the database (if alteration is a part of the upgrade) seamlessly.
Don’t miss to authenticate to the system console and enter the configuration password if applied – otherwise, agent support will not work.

Before installation of Java Cryptography Extension, please stop SecureAnyBoxServer service.
To install Java Cryptography Extension, you need to download a zip archive from the Oracle web. When downloaded, please extract files from the zip archive and copy jar files into a <SecureAnyBox folder>/jre/lib/security.
After installation, the SecureAnyBox Server service can start.
If the HTTPS keystore certificate is imported as trusted on your Linux station, it is possible to verify in the terminal using the command:
python -c 'import urllib2; import sys; resp = urllib2.urlopen("https://your.secureanyboxserveraddress.com"); rcode = resp.getcode(); body = resp.read(); print rcode; print ""; print body;'
If certificate validation is successful, on the first row of the response is code 200.
When the certificate validation fails, an error is displayed:
urllib2.URLError: <urlopen error [SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed (_ssl.c:590)>
If urllib2 not found
python ––version
Urllib2 is a built-in package of Python 2.x.x. To be able to run urllib2, it is necessary to have Python 2.x.x (recommended 2.7.18) installed properly. Some distributions of Linux may not have full version of Python 2.7.x installed. Try re-installing it.
wget https://www.python.org/ftp/python/2.7.18/Python-2.7.18.tgz
sudo tar xzf Python-2.7.18.tgz
cd Python-2.7.18/
sudo ./configure
sudo make altinstall
To install SecureAnyBox Agent on MAC OS platform, please run installer (secureanybox-agent-1.x.pkg).
At the third step of the installer, it is possible to change an install location, by clicking the appropriate button (
![]() ). To proceed with the installation, please click the
Install
button (
). To proceed with the installation, please click the
Install
button (
![]() )
)

After clicking the Install button, it is necessary to enter the user password to allow the installation.

Once the installation finished, information about the successful installation of the SecureAnyBox Agent is displayed.

When the installer closed, please go to the Launchpad where you can find the sab-config application.

Start the application by double click on its icon. When the application starts, please select the downloaded configuration file by clicking on the button (
![]() ). Once the configuration file selected, apply it by clicking an appropriate button (
). Once the configuration file selected, apply it by clicking an appropriate button (
![]() ).
).

To apply the configuration is necessary to enter your password.

After the configuration was updated, information about it displays, and SecureAnyBox agent successfully installed.

After the installation complete, SecureAnyBox Agent verifies that the applied Agent Configuration matches the configuration on the SecureAnyBox server. If so, the station will be registered automatically (it might take 10 minutes). If the SecureAnyBox Agent does not have access to the server, it is possible to register the station manually.
After successful installation, the SecureAnyBox starts and the initialization page displays. To login into a web interface, is required to set the admin password first.

In the
Security Code
field, is pre-filled unique code for your installation.
While entering the password, you can see how long your password is, how many lowercase letters, uppercase letters, numbers or other symbols password contains and how secure your password is.
The password has to be confirmed by clicking on the
OK
button. After confirming the password, the login page displays.
For a user to log into SecureAnyBox, the user needs to be created and has a password entered.
If more than one domain is specified, the user must also enter the domain name when logging in.

Only one domain set. To log in to the SecureAnyBox only username and password are required.
More than one domain set. To log in to the SecureAnyBox, it is necessary to enter a domain name also.
After entering the login credentials, a page for setting an access code displays. The access code is used to decrypt secured information (such as passwords, certificates) and to confirm changes.
While entering the access code, you can see how secure your access code is and also how many of the required characters you are using.

Actual/required length of access code
Actual/required number of lowercase letters
Actual/required number of uppercase letters
Actual/required number of numbers
Requirements to characters of the access code are possible to change in a configuration. More...
After the access code set, the page automatically redirects to the root level of Safe Boxes.
Automatic login by SecureAnyBox can be set for station default user only. Other users have to log in manually. This setting can be convenient for stations on which works more than one user, but the station primarily is used by a user with the lowest permissions. That user can be set as default and will automatically log on.
To set automatic login SecureAnyBox Agent on stations, please follow these steps:
Create Agent Configuration, where will be settings for all platforms of stations, on which you want install SecureAnyBox Agent.
At the Downloads page, please select appropriate Agent Configuration and download the SecureAnyBox Agent and it’s configuration.
Install SecureAnyBox Agent on a station.
Installation steps of SecureAnyBox Agent:
If in the Agent Configuration is set to change the password of a group, is necessary to have set local users group in which will be all users, who will be able to obtain the password from SecureAnyBox. Default user has to be set as one of them.
To create a local group of users in MS Windows, please follow these steps:
On the desktop, right-click My Computer, and then click Manage.
In the Computer Management window, under System Tools, expand Local Users and Groups.
Right-click Groups, and then click New Group.
In the New Group dialog box, do the following:
| Use this | To do this |
|---|---|
| Group name | Type the name of the group that you want to create. |
| Description | Optionally, type a description for this group account. |
| Add | Click Add to select members to add to the group. Add all the user accounts that you want to the group. |
Click Create.
Repeat steps 4 and 5 for the other required groups.
Click Close.
Click the Groups folder and verify that the group that you wanted to create are in the list.
Please set default user on your station.
If you want to update default user password by SecureAnyBox Agent, you need to have set a default user. Default user can log in to Windows automatically without entering his password.
To set default user for your station, please enter “netplwiz” into the Windows search field and click on the program in search results.

After clicking, User Accounts form displays. In a list of
Users for this computer, please click on a user which will be set as default (
![]() ), uncheck
Users must enter a user name and password to use this computer (
), uncheck
Users must enter a user name and password to use this computer (
![]() ) and confirm this modification by clicking on the
OK button (
) and confirm this modification by clicking on the
OK button (
![]() ).
).

After the restart of the station, the first automatic login should go through – the SecureAnyBox Agent sets the user’s password and changes it in the registers where the automatic login is stored. Password for default user can be obtained in SecureAnyBox at the Get Password page as for any other user.
In a case, that same default user set on more than one station; it is convenient to set changing a password for default user in the Active Directory domain. When all is set correctly, after the change of password of LDAP user, SecureAnyBox LDAP Agent checks all registered stations and where the user to whom the password changed set as default, the SecureAnyBox LDAP Agent changes a password for the station.
To update a password for default user in Active the Directory domain, please follow these steps:
Set Agent configuration for stations. In Agent configuration for LDAP platform set field Change password of to value default users in domain .

If you not have set App URL in general configuration of SecureAnyBox,it is necessary to set it in the Agent Configuration. App URL has to be accessible from the internet (out of local network). Without setting of App URL, the SecureAnyBox Agent can have problems with connection to SecureAnyBox server.
Configure LDAP Agent. In LDAP Agent select Active Directory as Directory service and prepare Active Directory server.

Into LDAP Agent select the Agent Configuration, which you created in the first step.
Into the Default user domain field, enter Active Directory domain name into which default user belongs, and if necessary, modify the User id attribute . Please configure other required values in LDAP Agent form and create LDAP Agent by clicking on the OK button. To apply the LDAP Agent is necessary restarting SecureAnyBox.
At the Downloads page, please select the Agent Configuration created in a first step and download the SecureAnyBox Agent and it’s configuration.
Please set default user on your station.
If you want to update default user password by SecureAnyBox Agent, you need to have set a default user. Default user can log in to Windows automatically without entering his password.
To set default user for your station, please enter “netplwiz” into the Windows search field and click on the program in search results.

After clicking, User Accounts form displays. In a list of
Users for this computer, please click on a user which will be set as default (
![]() ), uncheck
Users must enter a user name and password to use this computer (
), uncheck
Users must enter a user name and password to use this computer (
![]() ) and confirm this modification by clicking on the
OK button (
) and confirm this modification by clicking on the
OK button (
![]() ).
).

Install SecureAnyBox Agent on a station.
Installation steps of SecureAnyBox Agent:
After successful installation of SecureAnyBox Agent, a station should automatically register in the SecureAnyBox. Please check at the Stations page, that registration of the station ran successfully.

While registering, the SecureAnyBox Agent (for Windows), if the default user is enabled, sends default user information when registering (including the domain if it is a domain user). If the default user is a domain user, the SecureAnyBox Agent does not set the password – because it does not have permission to change the password of a domain user. In that case, a password of a domain user is set by the LDAP Agent.
The LDAP Agent scans all registered stations and retrieves from them default users whose domain is the same as default user domain specified in the LDAP Agent configuration. LDAP Agent generates and sets new passwords for these default users. This process takes place when you start the SecureAnyBox server, then every hour and after a click on the Execute button.
Depending on your configuration, users can authenticate via KeyShield SSO. For the automatic authentication, it is necessary to install the KeyShield SSO client on the station.
Instructions for unattended installation are at KeyShield_server/static/kshield_msi.page. For manual installation/configuration please follow screenshots:



The OES client for Windows integration works in a similar manner like former ClientTrust for BorderManager – KeyShield server creates a token and stores it as a value of an attribute of the user’s object. KeyShield client reads the value through the OES client for Windows API, uses it as a challenge, generates a response and sends it to the KeyShield server. Then the KeyShield server validates it and if OK, accepts the client authentication request and sends confirmation back to the client. Client changes the color of the icon in the taskbar to green to inform the user that authentication finished. Here is the related setting in the related eDirectory connector of the KeyShield server (keep in mind, you can use as many eDirectory trees, AD forests, etc. as you need at the time).

This is a so-called custom setup, but it is not necessary. The best practice is to let the KeyShield server to configure eDirectory connector automatically by choosing.
First, enter Connector ID and provide LDAP server IP and port.

Then click "Create KeyShield SSO objects"

KeyShield SSO will create own mgr account (proxy account used to access eDirectory), extend schema by auxiliary class (can be removed) for tokens and assign minimum access rights the mgr account needs.
Once you are done with this setting, the automatic authentication with the OES client for Windows should work. If not, consult Diagnostic log.
Importing the certificate is necessary for automatic registration of the station into SecureAnyBox via HTTPS protocol.
To import the certificate, please follow these steps:
Click Start and into Windows search field please enter “mmc” (
![]() ) and click on the program in the search results (
) and click on the program in the search results (
![]() ).
).

In the Console window, please click the
File (
![]() ) ->
Add/Remove Snap-in(
) ->
Add/Remove Snap-in(
![]() ).
).

Select
Certificates (
![]() ) in the left panel and click
Add (
) in the left panel and click
Add (
![]() ) to move a selection into the right panel. Then click the
OK button (
) to move a selection into the right panel. Then click the
OK button (
![]() ).
).

In the Certificates snap-in window, select
Computer account option (
![]() ) and click
Next button (
) and click
Next button (
![]() ). At the next window click the
Finish button (
). At the next window click the
Finish button (
![]() ).
).

In the Add or Remove Snap-ins window click
OK button (
![]() ).
).

In the Console window, expand
Certificates, and right-click
Trusted Root Certificates ->
All tasks ->
Import

In Certificate Import Wizard window click
Next (
![]() ), and at the next screen please select certificate to import (
), and at the next screen please select certificate to import (
![]() ). When certificate select, please click
Next (
). When certificate select, please click
Next (
![]() ).
).

Please enter the certificate password (
![]() ) and click
Next (
) and click
Next (
![]() ) and at the next windows click
Next (
) and at the next windows click
Next (
![]() ) and
Finish (
) and
Finish (
![]() ).
).


After import completed, the station should be registered into SecureAnyBox automatically (it may take 10 minutes). For immediate registration, you can restart SecureAnyBox agent service.
To install the certificate on a Mac platform, please download the certificate on your station and follow these steps:
To open Keychain Access, start by clicking on Go in the Finder menu and then select Utilities.
When the
Utilities window opens up, look for and click on the icon named
Keychain Access.
Note: Alternatively, you can open the
Keychain Access by typing “Keychain Access” in the
Spotlight search field at the top.
In the Keychains window select System.
Within the Keychain Access menu select File > click Import Items.
Browse to the .p12 or .pfx file that you want to import and open it.
Enter your admin password to authorize the changes and click Modify Keychain.
Enter the password that you entered when you created your .p12 or .pfx file.
Your SSL certificate should now be installed, and the station should be automatically registered.
Download KeyShield SSO certificate from the Certificate section of KeyShield SSO server.
On the server where SecureAnyBox installed please run a script in the format:
<SecureAnyBox Java folder>/bin/keytool -importcert -file <certificate file> -keystore <SecureAnyBox Java folder>/jre/lib/security/cacerts
where:
<SecureAnyBox Java folder> - is location of Java on which runs SecureAnyBox server (e.g.: /opt/tdp/secureanybox/jdk8/)
<certificate name> - is location of certificate file (if the script is running from a folder where the certificate file stored, just enter the name of the certificate file).
After certificate imported, it is possible to connect with KeyShield SSO server and save SecureAnyBox configuration successfully.
At first, install Chrome policy templates.
Run GPEDIT (gpedit.msc)
In the GPEDIT go to
Computer Configuration > Administrative templates > Google Chrome > Extensions > Configure the list of force-installed apps and extensions
(Extensions in the list are installed silently, without user interaction, and cannot be uninstalled nor disabled by the user)
Add SecureAnyBox Extension to the list in the following format:
jmjiclmedngjhklhcafhkmbhmdiecgif;https://clients2.google.com/service/update2/crx
Where text
jmjiclmedngjhklhcafhkmbhmdiecgif is the extension ID. For example, you can verify extension ID from the Chrome store address
Instead of using GPEDIT, you can write the settings directly into the windows registry.
Into key
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Google\Chrome\ExtensionInstallForcelist enter the value:
“1”="jmjiclmedngjhklhcafhkmbhmdiecgif;https://clients2.google.com/service/update2/crx"
At first, install Firefox policy templates.
Run GPEDIT (gpedit.msc)
In the GPEDIT go to
Computer Confguration > Administrative templates > Mozilla > Firefox > Extensions > Extensions to install
(Extensions in the list are installed automatically)
Add path to SecureAnyBox Extension file in one of following formats:
In the GPEDIT go to
Computer Configuration > Administrative templates > Mozilla > Firefox > Extensions > Prevent extensions from being disabled or removed
(Extensions in the list cannot be uninstalled nor disabled by the user)
Add SecureAnyBox Extension ID: sab_login@secureanybox.com
Instead of using GPEDIT, you can write the settings directly into the windows registry.
Into key
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Mozilla\Firefox\Extensions\Install enter the value:
“1”="http://<yourssecureanyboxserver.com>/swb/down/secureanybox-1.1.14-fx.xpi"
And into the key
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Mozilla\Firefox\Extensions\Locked enter the value:
“1”="sab_login@secureanybox.com"
SecureAnyBox stores subnets in the CIDR notation format.
The CIDR number comes from the number of 1’s in the subnet mask when converted to binary. You can refer to the following table to find the CIDR equivalent of your subnet mask.
| CIDR notation format | Dotted decimal format | Binary format |
|---|---|---|
| 32 | 255.255.255.255 | 1111 1111 1111 1111 1111 1111 1111 1111 |
| 31 | 255.255.255.254 | 1111 1111 1111 1111 1111 1111 1111 1110 |
| 30 | 255.255.255.252 | 1111 1111 1111 1111 1111 1111 1111 1100 |
| 29 | 255.255.255.248 | 1111 1111 1111 1111 1111 1111 1111 1000 |
| 28 | 255.255.255.240 | 1111 1111 1111 1111 1111 1111 1111 0000 |
| 27 | 255.255.255.224 | 1111 1111 1111 1111 1111 1111 1110 0000 |
| 26 | 255.255.255.192 | 1111 1111 1111 1111 1111 1111 1100 0000 |
| 25 | 255.255.255.128 | 1111 1111 1111 1111 1111 1111 1000 0000 |
| 24 | 255.255.255.0 | 1111 1111 1111 1111 1111 1111 0000 0000 |
| 23 | 255.255.254.0 | 1111 1111 1111 1111 1111 1110 0000 0000 |
| 22 | 255.255.252.0 | 1111 1111 1111 1111 1111 1100 0000 0000 |
| 21 | 255.255.248.0 | 1111 1111 1111 1111 1111 1000 0000 0000 |
| 20 | 255.255.240.0 | 1111 1111 1111 1111 1111 0000 0000 0000 |
| 19 | 255.255.228.0 | 1111 1111 1111 1111 1110 0000 0000 0000 |
| 18 | 255.255.192.0 | 1111 1111 1111 1111 1100 0000 0000 0000 |
| 17 | 255.255.128.0 | 1111 1111 1111 1111 1000 0000 0000 0000 |
| 16 | 255.255.0.0 | 1111 1111 1111 1111 0000 0000 0000 0000 |
| 15 | 255.254.0.0 | 1111 1111 1111 1110 0000 0000 0000 0000 |
| 14 | 255.252.0.0 | 1111 1111 1111 1100 0000 0000 0000 0000 |
| 13 | 255.248.0.0 | 1111 1111 1111 1000 0000 0000 0000 0000 |
| 12 | 255.240.0.0 | 1111 1111 1111 0000 0000 0000 0000 0000 |
| 11 | 255.224.0.0 | 1111 1111 1110 0000 0000 0000 0000 0000 |
| 10 | 255.192.0.0 | 1111 1111 1100 0000 0000 0000 0000 0000 |
| 9 | 255.128.0.0 | 1111 1111 1000 0000 0000 0000 0000 0000 |
| 8 | 255.0.0.0 | 1111 1111 0000 0000 0000 0000 0000 0000 |
| 7 | 254.0.0.0 | 1111 1110 0000 0000 0000 0000 0000 0000 |
| 6 | 252.0.0.0 | 1111 1100 0000 0000 0000 0000 0000 0000 |
| 5 | 248.0.0.0 | 1111 1000 0000 0000 0000 0000 0000 0000 |
| 4 | 240.0.0.0 | 1111 0000 0000 0000 0000 0000 0000 0000 |
| 3 | 224.0.0.0 | 1110 0000 0000 0000 0000 0000 0000 0000 |
| 2 | 192.0.0.0 | 1100 0000 0000 0000 0000 0000 0000 0000 |
| 1 | 128.0.0.0 | 1000 0000 0000 0000 0000 0000 0000 0000 |
An alias is an entry which points to another object in the namespace – by containing its dn. Searching the entry that an alias entry points to is known as dereferencing an alias.
There are four modes of dereferencing aliases:
In the directory have been set up two aliases:
In container “ou=People” are set up two other entries:
The following table summarizes the results of searching “ou=Employees” in different modes.
| Dereference mode | Results |
|---|---|
| Never | no entries (because the “ou=Employees” alias never dereferenced) |
| Dereference while finding the base object | no entries (because the “ou=Employees” alias never dereferenced) |
| Dereference while retrieving objects according to search scope | two entries: “cn = Marie Smith, ou=People” and “cn = Robert Norman, ou=People” (because the “cn=Newbie, ou=People” alias never dereferenced) |
| Always | three entries: “cn = Marie Smith, ou=People”, “cn = Robert Norman, ou=People” and "cn= James Black, ou=NewHires" |
| Password pattern | Entropy* | Generated passwords (examples) | |||
| 17 characters | |||||
| CvddcVcAzduldAAvl | 74.01 | zi02gIfKT5Ah7frys | Qo60histH3Pd4OQez | hi82xOpGQ7Ft1Lzef | |
| ZuAcVdAddcVlduldA | 72.65 | YLjvU9c67tol3Lc0P | ETGgO0B66zek9Xi3M | AIivE7q60kUr7Rt5y | |
| uzVcsAnVdACCvdAnC | 76.45 | NCur]g6o5Ygru3Y[t | CMul#F.A6mMfi8D(c | BMEx/y_A9SFTy4S5X | |
| dCVAAAAAdscVnuAnV | 76.70 | 7siJIsnK0/ce$Cy*E | 4WyKKsnr7$ky&Fu6A | 4koceFZL7;wo<Wm[u | |
| CvdscVcAznuldAAvl | 77.13 | Cy7)zYnVL5Vd4CYuo | Za0&tEmAW4Qc7Lbon | li7$rejUN*Og6Ixon | |
| 15 characters | |||||
| vddcVcAZduldAvl | 64.19 | o56xYtWU6He9Sal | a93vucrO8Gj5Oap | u58xYnAI5Be5uic | |
| AcdVAAVlCuldAdl | 66.02 | rz0ogHefmIf5A3w | Eh1aSfegCYt7t5w | pb1oPLYtPRg7P3n | |
| uZcdVCVCZuAVcdA | 65.94 | ZIn7eMawIHDYk5W | KAz9OCYgILLaz0t | GYx0YCyfYWpiv2c | |
| ZnAcVdnlAundCAV | 66.65 | A-LzI3:cPD;7SMy | U$Xby2:ecG45nlU | O4bpY6]wrQ71pMA | |
| dCVAccAdcVduAdV | 64.62 | 2gufrgC5by1Mm8u | 3ZeFtbv7pa2NY9A | 2Mavcqg2fO7Fa4u | |
| 12 characters | |||||
| CulllduCldVz | 53.25 | rHevf4DXy1EZ | bBuud7YKz2UM | cCbtg8Zsy5IB | |
| VAn*dAcVdlsu | 53.50 | Aj;O3mcy9b.H | Ex2<7gmE8i-O | UA2S8wry4y(W | |
| ZVdAsCVndldA | 52.34 | UA2p/SU58k7b | EO0C%HO@4s7r | OI5c:Se*8e2r | |
| uCldVdAsCVVA | 52.56 | Yxo8i3K>rUEF | ZNs3U6g/BuAX | Qwb6u6n&luYK | |
| AcVdlsCuldAd | 52.10 | lty8i%JHy6F5 | Cqu6t@xZk9m7 | Ymu9i$XRh9t0 | |
| Easier to remember (alternating consonants and vowels) | |||||
| cVcZdCvcddC | 46.32 | rumE9Zes04L | kurA7jas53d | tUlE8xiz14V | |
| cvVcdVddzZzV | 50.18 | hyoh6Y78DUPO | weyp8u59TYFA | viyr8u33PIQI | |
| cvcsdddcvcs | 45.35 | qab/141qor/ | cyh/582wut@ | guv$451vof@ | |
| CvcVsdcVcvd | 46.45 | GohI>5zini7 | juny/7xYdi3 | HamY&7dyqa4 | |
| zZzVdsdzZzV | 47.03 | PELa4[7TOQY | GIKo1@5KAKU | XAHa6#4NULa | |
* Password pattern entropy is counted as an average entropy of a hundred passwords that were generated based on the password pattern.
Password entropy is a measurement of how unpredictable a password is. The higher the value, the better.
Based on password entropy value, SecureAnyBox recognizes four levels of how secure the password is.
| Password security | min. | max. | Description | |
|---|---|---|---|---|
| really bad |
|
0 | 20 | password should be changed immediately |
| unsatisfactory |
|
20 | 35 | password does not meet security standards, should be changed |
| satisfactory | 35 | 50 | password meets security standards, but it can be better | |
| really good |
|
50 | password is really secure |
To specify a set of characters that will be
used while generating a password, please enter them into the field without any separator. (e.g., ‘abc’). In that case, the generated password will use only specified characters.
The set of characters that will be
omitted while generating a password must begin with ^ character (e.g., ‘^0123’). In that case, the generated password will use allowed characters except for specified ones.
In the Agent Configuration, it is possible to use a combination of 3 different Pattern Characters settings. Each character of the generated password can use only one setting.
Recommended steps:
| lowercase vowels | aeiouy |
| mixed case vowels | AEIOUYaeiouy |
| uppercase vowels | AEIOUY |
| lowercase consonants | bcdfghjklmnpqrstvwxz |
| uppercase consonants | BCDFGHJKLMNPQRSTVWXZ |
| mixed case consonants | bcdfghjklmnpqrstvwxzBCDFGHJKLMNPQRSTVWXZ |
| lowercase alphabet characters | abcdefghijklmnopqrstuvwxyz |
| uppercase alphabet characters | ABCDEFGHIJKLMNOPQRSTUVWXYZ |
| mixed alphabet characters | abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ |
| digits | 0123456789 |
| special charaters | .@&*()<>_][%$#/\?;-: |
You want to generate passwords that are user-friendly, without easily interchangeable characters (like 0 and O, or I and l and 1).
For such a password, enter
^0O1Il into Pattern Characters 1 field and into Password Pattern field enter as many ‘1’ as the number of characters the generated password should have.

This setting will generate passwords such as: vZ\Z7q@hoqiPK, C_6wsK((AujbG, K(_H-T*C]c%fq
If you want to ommit all special characters also, just add all special charaters to the text in Pattern Characters 1 field.

This setting will generate passwords, such as: 2a5CMpdGUXytD, Zs7aPYqSUV8ps, AxnXkr5KZhFYw
You want to generate easily readable passwords (with alternating consonants and vowels)
For passwords where characters are alternating is necessary to set two pattern characters settings. Into the first pattern characters enter all consonants and into the second one enter all vowels. The password pattern field will be set as alternations of 1 and 2. A number of 1 and 2 depend on how many characters the new password should have.

This setting will generate passwords, such as: fABOqucimac, minITafeJAl, NidedYvOKAt
You want to generate passwords that conform to the password requirements (for example, at least two capital letters, one number, or a special character)
For passwords that conform to the password requirements, it is necessary to set all characters that can be used in the generated passwords as Pattern Characters 1, upper case characters as Pattern Characters 2, digits, and special characters as Pattern characters 3.

As you can see on the image, in some cases, it can be simplier to specify characters to ommit. Text '^.&()<>_][%$#\?;:' has same effect as text 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789@-*/'

This setting will generate passwords, such as: vaDB3/smCVR, oFhV62MQEvI, RWXZl2HiGth